Anonymous file sharing: Stay private while sending files online

Sharing files online comes with real privacy risks, not just from cybercriminals or corporations, but sometimes even from the people you share with. In this context, anonymous file sharing can mean two things: keeping your files hidden from everyone except the intended recipient and keeping your identity hidden even from the recipient themselves.
Both forms of privacy matter, depending on your situation. This guide breaks down how anonymous file sharing works, the technologies behind it, like Tor and end-to-end encryption, and which tools help you stay private.
Whether you're a journalist protecting your sources or simply someone who values privacy, this guide will show you how to share files securely and discreetly. Let’s dive in.
What is anonymous file sharing?
Anonymous file sharing allows you to send or receive files without revealing your identity or personal information. It’s commonly used when privacy is a priority, whether for personal safety, security, or confidentiality. There are two main types of anonymity in file sharing:
| Sender anonymity | Private delivery |
| Your identity is hidden from the recipient and any third parties. This is primarily used by whistleblowers, journalists, or anyone who doesn’t want their actions traced back to them. | Only the intended recipient can access the file. Even if the sender’s identity is known, the file itself remains secure and hidden from outsiders. Useful for anyone sharing sensitive files such as their medical records or legal documents. |
Real-world scenarios (journalists, activists, legal cases)
Anonymous file sharing is used by individuals who handle sensitive information, especially when exposure could lead to surveillance, retaliation, or legal consequences. Below are key real-world contexts where data anonymity and data privacy matter:
Whistleblower protection
Anonymous file sharing plays a critical role in protecting whistleblowers. For example, an employee who uncovers misconduct or illegal activity at work will likely wish to report it without revealing their identity.
By using anonymous upload tools like Tor (which you can learn more about in our detailed Tor guide), they can submit sensitive evidence to journalists or authorities while minimizing their exposure.
Journalism
Reporters often work with whistleblowers, confidential informants, or politically sensitive material. If a file reveals the identity of a source, it could lead to harassment, job loss, or even imprisonment.
Activism
Activists operating in authoritarian environments need to share information discreetly to reduce the risk of identification. Anonymous sharing tools help them coordinate safely while reducing potential risks.
Legal cases
Lawyers and legal professionals often exchange highly confidential documents, evidence, contracts, or client records that must remain private. Leaking such information can jeopardize a case or violate attorney-client privilege.
Medical records sharing
In healthcare, the exchange of medical records between doctors, specialists, and patients involves deeply personal and often legally protected information. Private file-sharing services offer a secure way for patients to send test results, scans, or treatment histories without exposing their identity to third parties.
This is especially important for people managing chronic illnesses or sensitive conditions, who may need to consult multiple providers across different systems. With private sharing, they stay in control of their medical data, reduce the risk of breaches, and avoid unnecessary exposure.
Risks of using mainstream file-sharing services
Most popular platforms, like Google Drive, Dropbox, or OneDrive, are primarily designed for convenience and collaboration rather than for complete anonymity. They often log IP addresses, scan uploaded content, and require accounts linked to personal emails.
For example, when you upload a file on Google Drive and share the link, anyone who can access the file can also see the email address you used to upload it from their “Shared with me” folder, whether you intended for those details to be visible or not. In some cases, under applicable law, these platforms may be subject to data requests from governments or third parties, meaning your information could be accessed without your knowledge. And perhaps most importantly, they rarely protect your identity from the person receiving the file, making true anonymity difficult to achieve.
In some cases, under applicable law, these platforms may be subject to data requests from governments or third parties, meaning your information could be accessed without your knowledge. And perhaps most importantly, they rarely protect your identity from the person receiving the file, making true anonymity difficult to achieve.
For sensitive communications, these risks mean mainstream platforms may not provide the appropriate level of protection. Anonymous file-sharing tools can offer stronger safeguards by design.
What to look for when choosing a file-sharing app
Not all file-sharing apps are designed with privacy or anonymity in mind. If you’re handling sensitive information, here are the key features to prioritize:
- End-to-end encryption (E2EE): Ensures only you and the recipient can access the files. Even the service provider can’t read your data.
- Zero-knowledge architecture: The app should not store your passwords or have access to your encryption keys.
- No account required: Anonymous sharing options (e.g., via a link) add a layer of privacy, especially if you don’t want to reveal your identity.
- Open-source code: Apps with publicly available source code are generally more trustworthy, as their security can be audited by anyone.
- No metadata logging: Choose services that avoid storing IP addresses, timestamps, or other identifying info.
How to share files anonymously
Anonymous file sharing isn’t just about using the right tool; it's about following the right steps to protect your identity and the content you’re sending.
1. Connect to a VPN
Start by connecting to a reliable VPN that has a proven no-logs policy, such as ExpressVPN. A VPN masks your real IP address, which is what websites and services typically use to identify your location.
By rerouting your traffic through an encrypted tunnel, a VPN helps prevent your ISP, network administrators, or potential attackers from seeing what online service you’re accessing. (Learn more about what exactly your ISP can and can’t see when you use a VPN in our detailed guide on the topic.)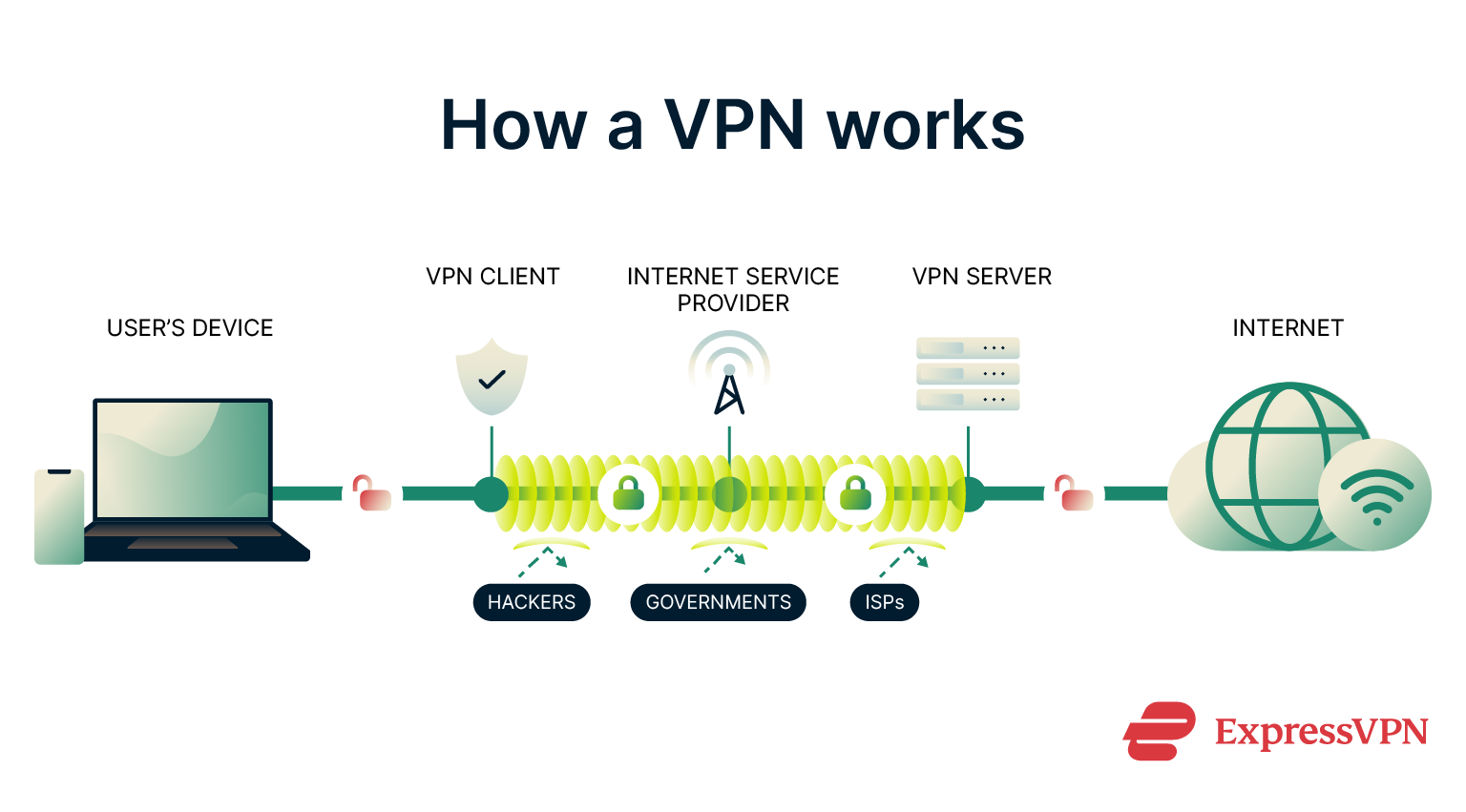 This makes it much harder to trace file-sharing activity back to you. It’s especially important if you’re using unsecured public Wi-Fi or operating in a sensitive environment. Even better, ExpressVPN provides an onion site, which allows easier and more secure access in restrictive environments, offering additional protection no matter where you are.
This makes it much harder to trace file-sharing activity back to you. It’s especially important if you’re using unsecured public Wi-Fi or operating in a sensitive environment. Even better, ExpressVPN provides an onion site, which allows easier and more secure access in restrictive environments, offering additional protection no matter where you are.
However, a VPN only protects your connection, not the file itself. Once a file leaves the VPN tunnel and lands on a server or in someone else’s inbox, you still need encryption and anonymity tools to keep it private.
2. Strip your files of metadata
Metadata is hidden information attached to your files, like who created or edited them, when, or even where a photo was taken. Even if the file itself is secure, this data can give away your identity.
Free tools like MAT2 for Linux or ExifTool for Windows and macOS can help by scanning your files for embedded metadata and letting you remove or edit it before sending anything.
3. Encrypt your files
Before sharing anything, encrypt it to protect the contents from prying eyes. Encryption transforms your files into unreadable data that only someone with the correct decryption key or password can access.
Tools like 7-Zip, VeraCrypt, or Cryptomator let you encrypt files or folders locally before sending them. However, you’ll need to share the decryption key with the intended recipient, ideally through a different channel than the one you use to send the files.
4. Choose a secure file transfer method and send your files
Here are some common privacy-first tools you can use for the main step: sending your files:
- Encrypted private email: These services typically combine end-to-end encryption, zero-access encryption, and anonymous sign-up. End-to-end encryption ensures that only you and your recipient can read the contents of your messages. Zero-access encryption ensures even stored emails are encrypted in a way that prevents the email provider’s servers from being able to decrypt them. Creating an account without providing any personal information allows you to use the service without revealing your identity.
- Tor file transfer services: Using one of these requires using Tor instead of or in combination with a VPN. Platforms like OnionShare encrypt your data so it’s unreadable during transfer, and they don’t upload anything to a central server. Instead, your computer acts as the source, and the recipient connects directly to it through a private Tor address. You don’t need the recipient’s email or phone number. Instead, you create a unique onion link that only they can access.
- Encrypted cloud storage: Services like File.io let you send and download files without an account. The service can encrypt everything, so even if someone accesses the server, the files should remain unreadable without your password. These are good when you want to store files safely over time or share them with multiple people.
VPN vs. Tor for anonymous file sharing
Both VPNs and Tor can help protect your identity when sharing files, but they work differently and suit different needs.
A VPN encrypts your internet traffic and routes it through a secure server, hiding your IP address from websites and your browsing activity from your ISP or anyone else monitoring your network. It’s fast, user-friendly, and ideal for sending files via cloud services or email.
Tor, on the other hand, bounces your connection through at least three volunteer-run servers (nodes). Because no single node knows both the origin and destination of your traffic, Tor reduces the need to place full trust in any single provider. That said, it still requires trust in the Tor network as a whole and in the software itself. Top-tier VPNs like ExpressVPN address similar trust concerns through measures like strict no-logs policies and independent security audits.
While Tor’s design can offer privacy advantages, it comes with a significant trade-off in speed. It’s generally much slower than a reputable VPN like ExpressVPN, whose Lightway Turbo protocol is specifically optimized for speed. This slower speed might not matter if you’re only sharing a few small documents, but if you need to upload gigabytes of files, it will take a very long time, and if the upload gets interrupted for any reason, you’ll likely need to do it all over again. In such cases, where large file uploads and faster speeds are important, a VPN can be the more practical choice
There’s one more consideration for users concerned about traffic correlation attacks due to the nature of the files they’re sharing. ISPs can see when you’re using Tor, just as they can detect VPN usage. However, since VPNs are far more common than Tor in most countries, using a VPN instead of (or on top of) Tor can make it harder to deanonymize you. This setup is especially helpful for whistleblowers or anyone sharing sensitive data while under surveillance.
Staying anonymous online beyond file sharing
Anonymous file sharing is just one part of protecting your identity. Here’s how to stay private more broadly:
- Use a VPN: It masks your IP address and encrypts your connection, making it much harder for anyone to see what you’re doing online.
- Use a privacy-focused browser: Browsers like Brave or Firefox block tracking and reduce your digital footprint.
- Avoid using personal accounts: Logging in via Google, Facebook, or similar services can expose your real identity.
- Be mindful of behavior patterns: Writing style, time zone, and language can reveal who you are. Vary your habits if anonymity is critical.
These tips will help you increase anonymity across your entire online presence, not just when sharing files.
FAQ: Common questions about sharing files anonymously
Is OnionShare really anonymous?
Yes, OnionShare is designed to be anonymous when used correctly. It runs over the Tor network, so your IP address is hidden, and it doesn’t require you to create an account or upload files to a central server. However, your anonymity also depends on how you use it. For example, sharing links over insecure channels or including identifying information in the file can still expose you.
Can I use OnionShare without Tor?
No, OnionShare relies on the Tor network to function, meaning it won’t work without it. The tool uses Tor’s hidden services to create a secure and anonymous connection between you and the recipient. This is what makes it possible to share files without revealing your IP address or relying on a central server.
How secure are anonymous chats?
The security of anonymous chats depends on factors like encryption, data collection, and whether the platform requires personal information. Highly secure anonymous chat apps use end-to-end encryption (E2EE), don’t require phone numbers or emails, and avoid storing logs or metadata that could identify users. Apps like Session or Briar offer strong anonymity and privacy protections, especially when used with a VPN or Tor.
However, some platforms that claim to be anonymous may still collect data or be vulnerable to surveillance or attacks, so it’s important to choose services carefully and avoid sharing personal information.
Is it legal to use anonymous file-sharing tools?
Yes, to the best of our knowledge, using anonymous file-sharing tools is legal in most countries. That said, what really matters is how you use them. Sharing copyrighted material, leaking classified documents, or distributing illegal content is still unlawful, regardless of the platform. However, using tools like OnionShare to communicate securely or share personal files is within your rights. If you’re unsure, it’s best to check local laws or regulations.
Is ToffeeShare a safe alternative?
ToffeeShare can be a safe option for peer-to-peer file sharing, but it has limitations. It uses end-to-end encryption and doesn’t store files on any server, which is intended to ensure that only the sender and recipient can access them.
However, it doesn’t offer anonymity by default; your IP address is exposed unless you use it with a VPN or Tor. It’s useful for quick, direct transfers but may not be suitable when full sender anonymity is required. For more private options, see tools that support anonymous file sharing by design.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN