What are anonymous proxies, and how do they work?

Tools like anonymous proxies claim to provide “total anonymity” by redirecting your online activity through a proxy server. But what level of privacy do they really provide?
In this guide, we’ll explain what an anonymous proxy is, the different types of proxies, when you can use one, and why a virtual private network (VPN) is a better option for your privacy.
Please note: No tool can make you completely anonymous online. Techniques like proxying and VPN tunneling can reduce the amount of information others see about you, but you can’t remove all forms of tracking, fingerprinting, or metadata exposure.
What is an anonymous proxy service?
When you type a URL into your browser or open an app, your device connects to the website or app’s server over the internet. In the process, your IP address becomes visible to the website or app and to your internet service provider (ISP), revealing your general location. And if tracking tools or cookies are being used, advertisers and other third parties might also be able to collect this data.
An anonymous web proxy service adds an extra step that hides this data. Instead of a direct connection between your device and your online destination, your browser connects to the proxy server, which then forwards your connection request. Now, the only identifying data tracks back to the anonymous proxy.
In theory, that sounds great, but in reality, the amount of information the proxy hides depends heavily on the proxy type and how it’s configured.
How do anonymous proxies work?
Anonymous proxies reroute your online requests through the proxy server. Your IP address is replaced with the proxy IP address, giving you some level of privacy and making it appear as if you’re connecting to the web from a different location.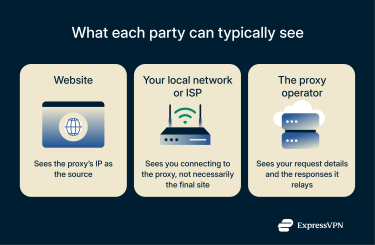
That said, most proxies don’t have any built-in encryption. In other words, when you use a proxy, your ISP will still see the same level of information about your activity, but just with a different target IP address. Also, the proxy operator will be able to see the data you send and receive. The bottom line is that it’s designed to hide who you are, but not to protect what you do or your data in transit online.
This is why protecting your connection with a quality VPN is a far better option; with a VPN, your entire connection is encrypted, and your activity is better hidden from your ISP and other third parties.
Request handling and IP masking explained
When you connect to a proxy, the process to handle your data and change your IP address happens nearly instantaneously. Here’s how it works:
- You go to a website or open an app: Your browser or app sends a request to reach the online service.
- The request is routed through the proxy: Instead of going directly to its destination, the request is rerouted to the proxy server.
- The proxy forwards the request: The request is now made by the proxy, acting on your behalf, using its virtual IP address.
- The website responds to the proxy request: The website or app sends the request back to the proxy server.
- You receive the response from the proxy service: You can access the content in your browser or phone as if you were connected directly.
While this process happens quickly, proxies in general add some lag and slow down your internet speed.
The proxy IP address can also affect what content you see. If the proxy server you use is in a different country or region from your physical location, the content, whether it’s search engine results, sports updates, or social media stories, will be from that location instead of your physical one.
How do websites detect proxies?
Websites can recognize proxy use in several ways:
- Proxy headers: Fields like Via or X-Forwarded-For can show the online traffic was routed through a proxy.
- IP reputation: Many proxy IP addresses belong to known data centers or public proxy networks, which are often listed in IP reputation databases. Websites can automatically block or challenge results from these ranges.
- Transport Layer Security (TLS) and connection patterns: Even without headers, fingerprinting techniques such as analyzing TLS handshake data or timing patterns can expose proxy usage.
If a website detects that you’re using a proxy, it might serve CAPTCHA challenges, limit functionality, or block access entirely. Some platforms flag proxy users as high risk and restrict transactions. Overall, using a proxy often reduces trust in the connection, and it generally offers limited privacy benefits.
Protocol-specific anonymous proxies
Anonymous proxies use various protocols to manage and route online traffic, and it’s important to understand the differences.
HTTP proxies
When you go to an unencrypted website, the proxy processes your request and responds directly. It hides your IP address but doesn’t encrypt your online traffic, leaving you vulnerable to monitoring and man-in-the-middle (MITM) attacks. It’s important to understand that sharing sensitive data on an unsecured HTTP website is extremely risky, and using an HTTP proxy will not improve your security.
HTTPS proxies
These proxies, also known as Secure Sockets Layer (SSL) proxies, work at the application layer (Layer 7) and support communication with encrypted websites. Unlike HTTP proxies, they forward encrypted traffic between you and the website without decrypting it. This keeps your data secure while masking your real IP address.
FTP proxies
These proxies are specifically used for transferring files via a File Transfer Protocol (FTP) server between clients and servers. They can help control or log uploads and downloads and are useful in a professional setting. FTP proxies aren’t encrypted, which means the data, including login credentials, can be intercepted if sent through an insecure connection.
SOCKS proxies
SOCKS proxies work at the session layer of the network (Layer 5), which means they can forward almost any kind of traffic, not just web browsing. This makes them versatile: they can handle email protocols like Post Office Protocol version 3 (POP3) and Internet Message Access Protocol (IMAP), file transfers via FTP, peer-to-peer (P2P) connections, online games, streaming apps, and chat platforms. The most common version, SOCKS5, supports authentication and works with both Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) traffic.
IRC proxies
Internet Relay Chat (IRC) proxies are used almost exclusively in online chats. They mask your IP address and are sometimes used to bypass connection restrictions on chat servers. However, this isn’t always effective, as some networks block known proxies. IRC proxies are mainly used in situations where users want to prevent IP-based bans and avoid exposing their real IP address to the IRC server or to other users in the chat.
Protocol-independent anonymous proxies
Some proxies operate on a larger scale and aren't limited to a single protocol. These protocol-independent proxies can handle various types of data traffic, making them more versatile across different types of devices and apps.
Proxy chains
Combining multiple proxy servers makes your data travel through several servers before reaching its destination. This multi-hop process adds multiple degrees of separation between your device and the target website, which makes the data harder to track or trace back to you.
The trade-off is speed and stability. Each additional server adds latency to the connection, resulting in slow speeds. It also increases the odds that there will be a compromised server in the proxy chain, causing the connection to drop and potentially exposing your data.
Mix networks
Mix networks, also known as mixnets, are an advanced form of proxy chaining. They batch, encrypt, and reorder messages. Then, they pass the data through multiple nodes at random. When done correctly, this makes it nearly impossible to know which data came from the sender or the receiver.
This is the base for tools like Tor, which use multiple nodes and layers of encryption to keep user data private. The downside is that the complex setup can significantly slow down your internet speed, and it's much more difficult to manage than a standard proxy. Mixnets are therefore more suitable for specialized cases, such as for whistleblower platforms and secure messaging.
Anonymous proxies vs. VPNs: Security and encryption compared
People who aren’t familiar with the technology behind these tools might assume that, since both an anonymous proxy and a VPN hide your IP address and change your apparent location, they’re essentially the same thing. However, a good VPN offers much stronger privacy by using secure tunneling protocols to encrypt all communication from your device.
Privacy and data protection
- Anonymous proxies replace your IP address with a proxy IP address. However, proxies don’t encrypt your information; they just forward it. While HTTPS websites still protect your data in transit, any data sent over an unsecured (HTTP) connection remains unprotected and open to interception. Some proxies introduce additional security risks.
- VPNs build a secure tunnel between your device and the VPN server. Everything you send is encrypted from the moment it leaves your device until it reaches that server, meaning your ISP, Wi-Fi owners, and anyone else on the network can’t see what you’re doing. Once your data arrives at the VPN server, it has to be decrypted so it can be sent to the website in a normal format. If the website uses HTTPS, its own encryption takes over immediately, so your data stays protected all the way to the destination. If the site doesn’t use HTTPS, there’s no second layer of encryption, so after the VPN’s layer is removed at the server, the data is sent out unencrypted. Even in that case, the important part is already protected: your identity, IP address, and all activity up to the VPN server stay hidden.
Security risks
- Anonymous proxies present multiple security risks. Many free or low-quality HTTP or web proxies log user activity, inject ads, or modify web content. Since the online traffic isn’t encrypted, they’re a frequent target for hackers and can easily leak sensitive information.
- VPNs have multiple tools designed to prevent security vulnerabilities. ExpressVPN comes with a built-in kill switch, Domain Name System (DNS) and Web Real-Time Communication (WebRTC) leak protection, and a no-logs policy, and it has undertaken multiple independent security audits to verify its protections.However, not all VPNs are created equal. Some introduce the same risks as low-quality proxies. They may log user activity, share data with third parties, or even inject ads and malware. This is why it’s important to choose a trusted provider.
DNS leaks
- Anonymous proxies don’t manage DNS requests. Your device sends DNS queries through your regular ISP before the proxy connection is made. This exposes the domains you visit to your ISP or network administrator.
- VPNs prevent DNS leaks by encrypting and routing DNS queries through their own secure servers. ExpressVPN uses private, zero-knowledge DNS on every server, ensuring that your browsing activity and DNS lookups remain completely protected.
Performance and reliability
- Anonymous proxies only work with specific apps or browsers, and free versions are often slow due to congestion or disconnect from downtime.
- Reputable VPNs route all traffic through optimized, high-speed servers designed to balance encryption and performance.
Anonymous proxy use cases
As long as you're not engaging in any sensitive activities that you'd want to keep private, there are some legitimate use cases for an anonymous proxy in personal and professional settings. Here are some of the common ways that individual users and businesses apply them.
Personal use
Here are a couple of reasons that home users might choose an anonymous proxy.
Accessing home or regional content
Some websites show different content depending on a visitor’s IP address. When someone travels abroad and uses a proxy that assigns an IP from their home region, the site may display the version of the content intended for that region.
Avoiding targeted or personalized content
Websites and social media sites use retargeting to funnel specific types of content based on what you’ve read in the past. Using a proxy masks your IP address, which can limit some location-based targeting, but it doesn’t stop personalization entirely. In particular, logging into an account will allow the platform to track your activity across sessions, so personalized recommendations, ads, or content will still be based on your account history rather than your IP.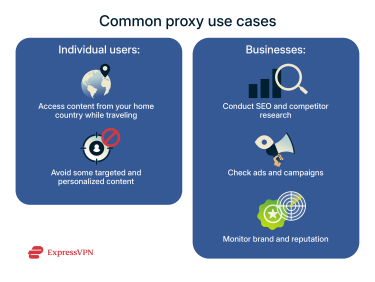
Business use
Businesses use anonymous proxies for various purposes; here are some common ones.
SEO and competitor research
Search engines give local results and tailor them to your search history, which can make it difficult to see how your company or your competitors rank in different regions. Using proxies with IP addresses from different countries lets you view search results as if you were browsing locally in that region, helping reduce personalization bias.
Ad verification and campaign monitoring
Advertisers use anonymous proxies to see how ads appear to users in different markets. Connecting through a proxy allows testers to view ads as they’d appear to local audiences, reducing location-based bias and preventing ad networks from tailoring results to the tester’s usual profile.
Brand and reputation monitoring
Companies use anonymous proxies together with monitoring tools to check for trademark misuse, counterfeit listings, or negative mentions without alerting the source.
That said, a VPN effectively serves all of these work-related purposes.
Risks and limitations of anonymous proxies
While the above use cases are legitimate, anonymous proxies aren’t without risk. And in most cases, a reputable VPN can accomplish the same tasks but lowers the risk.
Potential security and privacy risks
The lack of encryption with anonymous proxies is a huge red flag. Without encryption, your data travels in plaintext and can be viewed by the proxy operator, your ISP, and malicious actors. Even if you’re browsing on an HTTPS site, some proxies can intercept your online traffic, breaking encryption and exposing sensitive data such as passwords or payment information.
Free proxies are especially risky; common activities include:
- Logging or selling user activity to advertisers or third parties.
- Injecting ads or tracking scripts into the web pages you visit.
- Distributing malware or phishing links through proxy landing pages or browser extensions.
Legal implications and compliance
The legality of using anonymous proxies depends on where you live and how you use them. Accessing blocked content, bypassing corporate restrictions, or scraping data from websites can violate local laws, company policies (and even your employment contract), as well as a site’s terms of service (ToS).
Organizations using proxies for data collection or monitoring must also ensure they comply with local data protection laws such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), which require transparency and consent when handling user data.
If you’re unsure about the legality in your jurisdiction, consult with a lawyer before using a proxy, especially for commercial purposes.
FAQ: Common questions about anonymous proxies
Is it legal to use anonymous proxies?
In most countries, using an anonymous proxy is legal as long as you’re not using it to commit a crime or violate a website’s terms of service (ToS). However, some governments restrict or monitor proxy use. Always check local regulations or consult with a lawyer beforehand to avoid any legal issues.
Can anonymous proxies be traced?
While an anonymous proxy can hide your IP address, your activity can still be traced. Since proxies generally don’t encrypt your traffic, your activity can be tracked through logs kept by the proxy provider, browser leaks, or other tracking methods such as cookies or fingerprinting.
What is the difference between anonymous proxies and VPNs?
The biggest difference is encryption. Trusted VPNs create a secure, encrypted tunnel between your device and the VPN server, protecting all your internet traffic. Anonymous proxies typically only mask your IP address and don't encrypt your traffic, leaving it potentially visible to your internet service provider (ISP) and other third parties.
Are free anonymous proxies safe to use?
This depends on the service, but free anonymous proxies often don’t have secure protocols like HTTPS or SOCKS, and some record or sell user data to third parties. Web proxies can also inject ads, use tracking scripts, and expose you to malware.
Do proxies encrypt my internet traffic?
Anonymous proxies don’t encrypt your traffic. They simply route it to a different IP address to mask your location. If you’re visiting an HTTPS site, the connection between your browser and the site is encrypted. However, you should always be cautious when using free or unknown web proxies, as they may intercept and reencrypt the connection, which can expose sensitive data.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN