End-to-end encryption: What it is and why it matters


Encryption is essential for securing digital communications. Without encryption, every message, photo, or file you send online could be intercepted and accessed by malicious third parties. Thankfully, end-to-end encryption (E2EE) can protect your data while it’s in transit.
E2EE ensures that only you and the intended recipient can access your communications. It secures everything from instant messages to emails and cloud storage, and it’s a cornerstone of modern-day privacy and security.
Knowing how E2EE works and why it’s important can help you choose the right apps and services for daily use. This guide will explore the fundamentals of E2EE, its real-world applications, and why it is essential for safeguarding your digital communications.
What is end-to-end encryption (E2EE)?
Encryption is the art of keeping messages secret, and it has a rich history dating back to ancient times. E2EE is a modern version of encryption that secures communication and prevents third parties from accessing data while it’s in transit.
E2EE encrypts data on the sender’s device before it’s transmitted and ensures that the decrypted information is only available on the recipient’s device while remaining encrypted during transmission.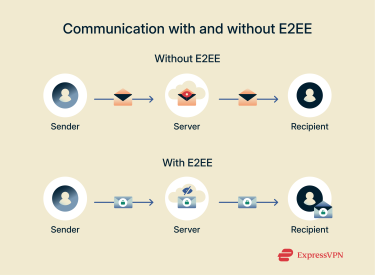 You can understand the core principle of E2EE by imagining sending a letter inside a locked, tamper-proof box that only you and the recipient have the keys to. Even though the box passes through many hands, such as postal workers, sorting centers, or delivery services, none of them can open the box or see what's inside. Only the intended recipient, with their unique key, can unlock the box and read the message.
You can understand the core principle of E2EE by imagining sending a letter inside a locked, tamper-proof box that only you and the recipient have the keys to. Even though the box passes through many hands, such as postal workers, sorting centers, or delivery services, none of them can open the box or see what's inside. Only the intended recipient, with their unique key, can unlock the box and read the message.
How end-to-end encryption works: Step by step
The steps below highlight how E2EE ensures that information is safely transmitted from one user to another.
Step 1: Encryption at the sender's device
The first step in E2EE involves your device using an encryption algorithm to transform your data into unreadable ciphertext, securing it before it’s even transmitted. This process uses a unique cryptographic key, and only the intended recipient possesses the corresponding key needed to unlock and read the message.
Step 2: Data transmission over a network
Once encrypted on your device, the ciphertext is transmitted across a network. This journey can be through the internet, cellular networks, or Wi-Fi. No one can see your data during transit because only your recipient possesses the necessary decryption key. Any servers or services that handle the data will only see the unreadable ciphertext.
Step 3: Decryption on the recipient's device
Once the data arrives on the recipient’s device, the last step is to decrypt it. Depending on whether symmetric or asymmetric encryption is used, either the recipient’s private key or the shared key is used to decrypt the data so the recipient can read and access it.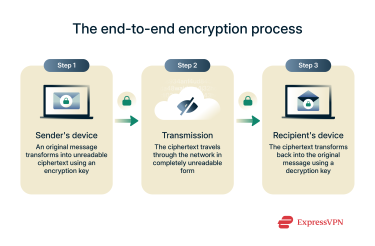
Symmetric vs. asymmetric encryption
Depending on the implementation, E2EE can use asymmetric encryption (two different keys), symmetric encryption (single shared key), or a combination of the two approaches.
Symmetric encryption is when a single key is used for both encryption and decryption. Since there’s only one key involved in the process, a secure key exchange mechanism is essential to ensure third parties can’t grab the key and gain unauthorized access to data. Symmetric encryption is fast at encrypting vast amounts of data and is more mature than asymmetric encryption.
Asymmetric encryption, also known as public-key encryption, uses a pair of mathematically linked keys called public and private keys. In E2EE, the public key is used to encrypt data and can be freely shared, while the private key is used for decryption and must be kept secret. Data encrypted with a public key can only be decrypted with its corresponding private key. This approach addresses the key exchange challenge found in symmetric encryption.
Hybrid approaches combine symmetric and asymmetric encryption to get the benefits of both added security and increased efficiency. In a hybrid system, a symmetric key is used to encrypt the actual data, but the key itself is encrypted and shared via asymmetric encryption.
Authentication
Authentication is a key aspect of E2EE, as it’s used to verify the identities of the communicating parties and ensure you’re exchanging messages with the intended recipient.
Without authentication, even if messages are encrypted, a malicious actor could intercept the communication and pretend to be one of the parties. This is known as a man-in-the-middle (MITM) attack.
Key exchange methods
In cryptography, key exchange methods allow two parties to safely share keys for data encryption and decryption. The type of key exchange depends on whether symmetric or asymmetric encryption is used.
For symmetric encryption, common methods of key exchange include:
- Pre-shared keys (PSK): PSK are simply keys that are exchanged by the parties before the communication.
- Manual key exchange: This method involves the manual physical transfer of keys between parties.
Asymmetric encryption has more sophisticated key exchange methods, including the following:
- Diffie-Hellman (DH): A method that uses modular arithmetic to allow two parties to establish a shared secret key over an insecure channel without directly transmitting the key.
- Elliptic Curve Diffie-Hellman (ECDH): A variant of DH that uses elliptic curve cryptography, offering equivalent security with smaller key sizes and reduced computational overhead.
E2EE-related standards
There are various E2EE standards used by organizations to secure communications. Below are some of the most noteworthy standards powering modern-day E2EE:
- Advanced Encryption Standard (AES): AES is a highly trusted symmetric-key encryption algorithm developed by the National Institute of Standards and Technology (NIST). It’s trusted by security experts worldwide, and it drives ExpressVPN’s own security.
- Signal Protocol: Formerly known as TextSecure Protocol, the Signal Protocol is what privacy-first messaging apps like Signal use to safeguard communications. It combines multiple cryptographic techniques, including the Double Ratchet algorithm and Extended Triple Diffie-Hellman (X3DH), to ensure messages stay private with forward secrecy.
- OMEMO Multi-End Message and Object Encryption (OMEMO): This is an XMPP Extension Protocol (XEP) for secure multi-client E2EE (where a user accesses a service from multiple devices or clients). Based on the Signal Protocol, it’s an open standard that can be freely used and implemented by anyone.
- Message Layer Security (MLS): MLS is an open standard for end-to-end encrypted group messaging, offering forward secrecy, post-compromise security, and easy scaling for large, dynamic groups. This makes it a strong foundation for modern secure messaging apps.
Real-world applications of E2EE
E2EE plays a key role in securing many services we use daily, including cloud storage, instant messaging, and email. Its ability to secure communications from sender to recipient makes it invaluable across various platforms. Understanding where E2EE is implemented can help you identify and choose services that prioritize your privacy and data security.
Private messaging apps
Messaging applications are arguably the most common and impactful real-world application of E2EE. The top security-first messaging apps like Signal, Wickr, and Wire all use E2EE to secure communications between users, ensuring no one except the sender and recipient can see any information in sent messages.
Email services
The most secure email services available use E2EE to safeguard the contents of emails. Since you often receive sensitive data over email, like banking information, password reset emails, and more, it’s a good idea to consider using an end-to-end encrypted email service for safety.
While Google is yet to implement E2EE for personal email accounts, it has introduced it for enterprise users.
Cloud storage
While it isn’t included with every top cloud storage solution, E2EE has started to become a key part of cloud storage security, with reputable providers like Dropbox providing it as part of their solutions.
When E2EE is applied to cloud storage, your files are encrypted on your device before they’re sent to the cloud provider's servers. This is especially helpful if you have sensitive data to back up, as it ensures that not even the cloud storage provider can see it.
Password managers
Considering how password managers store lots of sensitive information, such as your logins, card details, addresses, and more, it’s no surprise that E2EE is a key part of these tools. ExpressVPN Keys and other reputable password managers use E2EE as the groundwork for their zero-knowledge architecture, which ensures no one but you can see what’s in your vault.
Benefits of E2EE
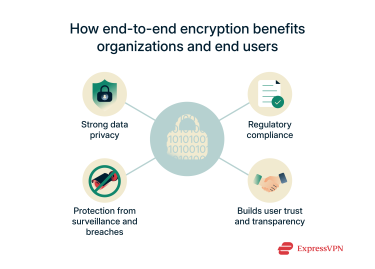
Strong data privacy
By encrypting data at the endpoints, E2EE guarantees that only the communicating parties can read the messages, blocking unauthorized access from cybercriminals, service providers, or other third parties. This protects sensitive information such as financial transactions, medical records, and confidential business discussions from exposure.
Protection from surveillance and breaches
Since E2EE can keep data encrypted in storage, it’s a reliable defense against potential data breaches. Even if servers or networks are compromised, attackers can’t decipher the encrypted data without the private keys. Of course, the fact that data remains encrypted during transit means that anyone attempting unauthorized surveillance can’t spy on your activity either.
Regulatory compliance
Among the significant benefits of E2EE is the fact that it helps ensure compliance with privacy regulations like the EU’s General Data Protection Regulation (GDPR) and the U.S. Health Insurance Portability and Accountability Act (HIPAA). While these regulations don’t mandate encryption for most data, the safety benefits provided by E2EE help safeguard sensitive personal information, which is a key requirement of such regulations.
Builds user trust and transparency
Implementing E2EE builds significant user trust and fosters transparency in digital services. When platforms use E2EE, users don’t have to rely solely on the service provider's promise that they won't read their messages, because the encryption makes it technically impossible for the service to do so.
Legal and ethical considerations of E2EE
While E2EE provides unparalleled privacy and security benefits, its widespread adoption also raises legal and ethical questions.
Is E2EE legal worldwide?
The legality of E2EE varies globally. Many countries recognize the importance of strong encryption for protecting privacy, digital communications, and securing business activities. However, some have sought to restrict or regulate its use.
Overall, the legal landscape is highly fragmented, with some countries supporting strong encryption and others enacting measures that could erode its protections.
Ethical debates: Privacy vs. security
The ethical debate around E2EE often centers on the perceived tension between individual privacy and public safety. Advocates for privacy argue that strong encryption is essential for protecting human rights, enabling free expression, and safeguarding personal data from surveillance, hacking, and misuse, particularly in environments where privacy is not guaranteed.
On the other side, some in law enforcement contend that encrypted communications can hinder criminal investigations and pose challenges to public safety. They argue that greater access is needed to prevent and respond to crime, though this access would require weakening or bypassing encryption, raising concerns among privacy and security experts about the broader risks such measures could introduce.
How do global regulations like GDPR affect E2EE?
The GDPR requires any organization handling the data of EU citizens to implement appropriate technical and organizational measures to secure personal data. While it doesn’t define the specific technical methods that organizations should use, E2EE is widely recognized as a security measure that can help organizations to comply with GDPR data management standards.
Limitations and challenges of E2EE
Metadata is not usually encrypted
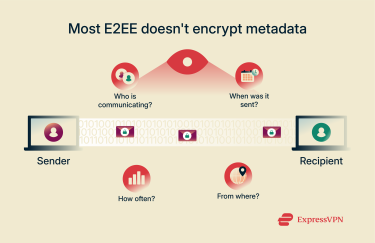
A significant limitation of most E2EE implementations is that they don’t encrypt metadata. Metadata includes crucial details about communication, such as who communicated with whom, when, how often, and from where. While the content of a message might be secure, this accompanying information can still reveal significant patterns about an individual's life and relationships.
Even without accessing the message content, analyzing metadata can provide information for surveillance. For example, knowing that someone frequently communicates with a specific individual at certain times can infer relationships or activities. This unencrypted metadata represents a potential privacy vulnerability that E2EE does not address.
That said, some apps overcome this limitation. For instance, Signal’s Sealed Sender functionality also encrypts much of the metadata involved in user communications, thus enhancing privacy and security further.
Key management issues
The secure management of cryptographic keys presents a persistent challenge in E2EE systems. For E2EE to function, users must securely manage their private keys, which are essential for decrypting data. For instance, losing your master password for a password manager might cause you to permanently lose access to your vault.
Additionally, if a private key is stolen or compromised, an attacker could decrypt past and future communications, completely undermining the encryption's purpose. However, this can be prevented if an application implements perfect forward secrecy (PFS) alongside E2EE. PFS generates new keys for each session, ensuring prior communications remain inaccessible even if one key is compromised.
Endpoint security remains a weak link
Although E2EE safeguards data during transmission, the security of the endpoints remains a crucial vulnerability. If a user's device is compromised by malware or a malicious third party gets physical access to it, the unencrypted data can be accessed before it’s encrypted or after it’s decrypted.
Not fully future-proof
Current E2EE methods are not necessarily future-proof against all emerging threats, such as quantum computing. Powerful quantum computers could theoretically break many widely used cryptographic algorithms like Rivest–Shamir–Adleman (RSA), which form the basis of current E2EE key exchange.
While practical quantum computers capable of breaking current encryption are still some years away, the potential threat necessitates research into "post-quantum cryptography." An example of this future-proofing is ExpressVPN’s post-quantum protection, which aims to safeguard users’ online privacy against these emerging threats.
E2EE vs. other encryption methods
It is important to distinguish E2EE from other forms of encryption to fully understand its applications. While various encryption methods protect data at different points, E2EE provides a distinct level of security that other methods may not.
Is TLS the same as E2EE?
While Transport Layer Security (TLS) and E2EE operate in a similar manner, they’re not quite the same. TLS primarily secures the connection between a client (like your web browser) and a server: when you visit a website with HTTPS, TLS encrypts the data as it travels across the internet to the server. In contrast, most E2EE implementations are between two users, not between a server and a client.
Additionally, with TLS, once the data reaches the server, it’s typically decrypted there and remains in this state. This means the server owner could potentially see the data in its unencrypted form.
Is E2EE more private than server-side encryption?
Server-side encryption encrypts data on the service provider's servers before it’s stored. While this protects data at rest and prevents unauthorized access if the physical storage is compromised, it’s less private than E2EE because the service provider itself holds the keys and can access the unencrypted data.
E2EE vs. S/MIME
Secure/Multipurpose Internet Mail Extensions (S/MIME) uses public key encryption and allows for the encryption and digital signing of emails to secure them. It’s similar to E2EE in that only the intended recipients can decrypt the data in the emails using their private key.
The drawback to S/MIME compared to the current E2EE standards used in most apps is that users must obtain digital signatures from certified authorities in order to use the standard.
E2EE vs. PGP
Pretty Good Privacy (PGP) is a well-established and effective cryptographic protocol that provides security and privacy for communication. PGP uses a combination of asymmetric and symmetric cryptography, which balances speed with security, as discussed earlier.
The downside to PGP compared to the E2EE used in most current apps is that it requires significant technical knowledge for setup and key management. In contrast, E2EE implementation in modern apps like WhatsApp is user-friendly and doesn’t require any technical knowledge to use.
FAQ: Common questions about end-to-end encryption
Can end-to-end encryption be hacked?
While breaking the encryption algorithms themselves isn’t technically feasible, no method of security is foolproof. The endpoints in end-to-end encryption (E2EE), where data is encrypted and decrypted, remain vulnerable. If these endpoints are compromised via malware or social engineering, communications could be intercepted.
Should I use end-to-end encryption for my messages?
Yes, you should consider a messaging service that uses end-to-end encryption (E2EE). This protects your conversations from unauthorized access by third parties, including internet service providers, malicious actors, and even the companies that provide the messaging service.
How do I turn off end-to-end encryption in WhatsApp?
You can’t turn off end-to-end encryption (E2EE) for any of your WhatsApp chats. However, it’s completely optional to have E2EE enabled for your WhatsApp chat backups.
Is end-to-end encryption used in WhatsApp and Signal?
Yes, both WhatsApp and Signal use it to safeguard your communications. However, there are some key differences worth noting. The first is that Signal also encrypts metadata through its Sealed Sender technology, while WhatsApp only encrypts the actual communications.
Additionally, Signal’s implementation of end-to-end encryption (E2EE) is completely open-source and can easily be audited, while WhatsApp uses proprietary technology. WhatsApp is also owned by Meta, which has a reputation for collecting substantial quantities of user metadata.
What are the risks of not using end-to-end encryption?
Not using end-to-end encryption (E2EE) for your communications carries significant risks. Without it, your messages and data could be intercepted and read by various unauthorized parties during transmission, such as your internet service provider (ISP) or potentially malicious third parties.
Does end-to-end encryption slow down performance?
It depends. It’s true that encryption adds computational overhead due to the computing resources required to encrypt and decrypt data. However, it’s unlikely to reduce performance unless substantial quantities of data need to be encrypted or decrypted.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN