
If you’ve ever switched to a new phone number, chances are your old number will be reassigned to someone else.
This practice of recycling phone numbers is standard, but it poses a significant privacy and security risk, as a recent study found. Not only are recycled phone numbers incredibly easy to obtain, but they can also be used to stage a myriad of attacks on their previous owners, ranging from account takeovers and phishing and spam attacks, to even preventing new owners from signing up to online services and asking for ransom to release the number.
How the attacks work
The study outlines eight types of attacks, but the simplest and cheapest method to execute is the reverse lookup attack. Here, attackers use the carrier’s online interface to try to identify a recycled phone number, buy it, and use it to access a victim’s account linked to that number.
This can be done if the victim uses SMS for two-factor authentication (2FA) and hasn’t updated their phone number. Out of the 259 phone numbers evaluated, 66% were “vulnerable to account hijackings at six popular websites: Amazon, AOL, Facebook, Google, Paypal, and Yahoo,” and 39% were “linked to leaked login credentials on the web, which could enable account hijackings that defeat SMS multi-factor authentication.”
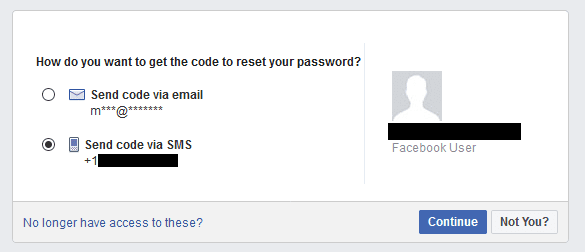
So if, for example, you were using SMS 2FA on Facebook, and a Facebook leak exposed an old phone number linked to your account, someone could gain access to your account, reset your password, and lock you out of your account.
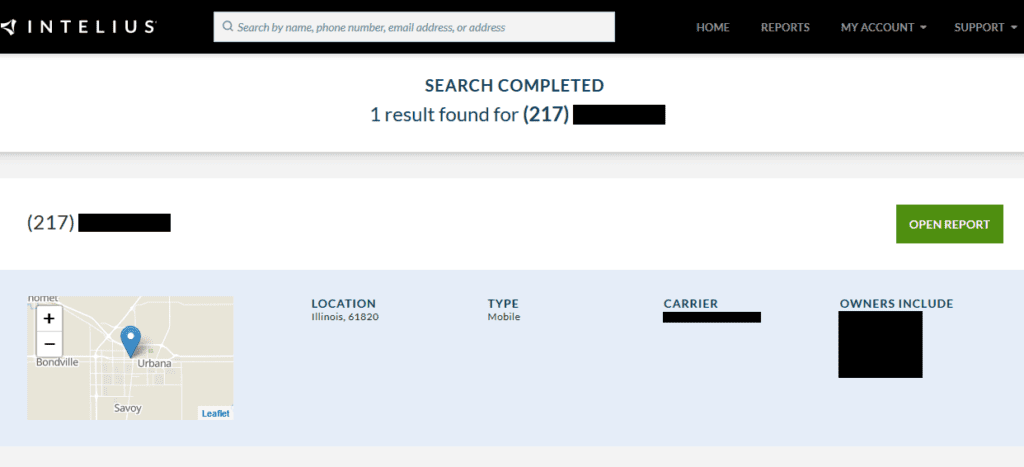
Even more alarming is that 66% of those phone numbers could also be used to find personally identifiable information like the name and location of the previous owner on people search services like BeenVerified or Intelius.
There are five additional number-recycling exploits also outlined in their study that target both previous and future owners, allowing an attacker to impersonate previous owners, hijack online accounts, and execute denial-of-service attacks.
Millions of old phone numbers, easy to exploit
According to the Federal Communications Commission, 35 millions phone numbers are disconnected in the U.S. every year. These phone numbers then appear on number change interfaces on mobile carrier websites like Verizon and T-Mobile, which not only allow you to cycle through an endless supply of numbers, but also see the entire number before changing too. This allows attackers to find and exploit these numbers before they’re selected by future users.
The study did reach out to U.S. carriers with their findings. T-Mobile and the Cellular Telecommunications Industry Association now remind users to update their contact information on all their accounts linked to the old number when they get a new one. The study also points to several things users can do to protect themselves from such attacks, namely…
Stop using your phone number for 2FA
This study is further evidence to show how risky SMS-based authentication can be, especially as attackers don’t even need to know your password to reset and access your account when using your phone number.
If you do need to change your phone number, the study recommends you do the following:
- Unlink your phone number from online services first.
- Use a secure alternative to SMS, like authenticator apps or even hardware keys if possible.
- Consider using a low-cost number “parking” service that allows you to keep your old number.
[Get more security tips and tricks. Subscribe to the ExpressVPN Blog Newsletter.]
Data leaks are increasing in scale and frequency, exposing details of hundreds of millions of people connected to social media platforms and other online services. With leaks aiding malicious actors in exploiting this information for personal gain, it is even more important now to maintain control over the security and privacy of your accounts.
Use a 2FA app, opt out of online services and databases that share your personal information publicly, check your privacy and security settings on your devices, and reconsider the services you currently use.
Read more: How to delete your online accounts
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN
















Comments
When it asked how you want to be notified to reset password its not letting me flag email address.