IoT cybersecurity: What it is and why it’s critical for modern networks

Most Internet of Things (IoT) devices don't have built-in security like regular computers or smartphones do. They may use old firmware, weak authentication, and lack encryption or automatic software updates. These gaps make them easy targets, and once compromised, a single IoT gadget can help attackers infiltrate entire networks, steal sensitive data, or disrupt operations.
That's why it's so important for modern networks to have IoT cybersecurity. In this article, we’ll explain what it means, the unique challenges it faces, and the best strategies you can use for protecting IoT devices from vulnerabilities and threats.
What is IoT cybersecurity?
IoT cybersecurity is the set of rules, technology, and practices that protect IoT devices, their data, and the networks they connect to from digital threats. It includes everything from secure device design and firmware updates to network controls, monitoring, and incident response.
IoT security vs. cybersecurity: What's the difference?
Although the terms are often used interchangeably, IoT security and IoT cybersecurity focus on slightly different aspects of protecting connected devices.
IoT security is the broader concept. It covers everything involved in keeping IoT devices safe, from the physical hardware and embedded software to their configuration and deployment. This includes secure manufacturing processes, tamper-resistant hardware, strong authentication, and safe default settings.
IoT cybersecurity, on the other hand, focuses on defending IoT systems against digital threats. It focuses on protecting communication channels, preventing unauthorized access, detecting malware, encrypting data, and monitoring device behavior across the network.
Key concepts: Attack surface, network exposure, threat models
To understand why IoT environments are harder to secure, it helps to look at a few core concepts that shape their overall risk:
- Attack surface: The set of all points where an attacker could attempt to compromise an IoT system.
- Network exposure: The degree to which an IoT device or system is accessible over a network.
- Threat models: Outlines who might attack the IoT system, how they might do it, and what they might target.
Why IoT devices require unique cyber protection
IoT devices need specialized protection because they introduce unique security challenges. This is due to several inherent vulnerabilities that make them easier targets for attackers compared to traditional computing systems.
Resource limitations
Many IoT devices run on lightweight chips with limited RAM, leaving little room for strong encryption, behavioral monitoring, or advanced security controls. Over time, this creates predictable weaknesses that attackers know how to exploit.
Long lifecycles with inconsistent updates
Devices often stay in use for years, long after vendors stop providing firmware patches. This leaves aging devices running outdated, vulnerable code.
Operational complexity at scale
IoT environments can involve hundreds or thousands of devices. Every device needs onboarding, configuration, monitoring, and maintenance, and doing this consistently across a large, dispersed fleet is challenging.
Diverse hardware, operating systems, and protocols
Standardized security practices rarely apply cleanly across such different technologies. A fix for one device model may not work for another.
Configuration inconsistencies
Typical IoT infrastructure often mixes old and new devices with different firmware versions, custom settings, and security defaults. This creates uneven protection throughout the environment, and attackers only need to find the weakest link.
Physical tampering
Some IoT devices sit in public areas, factory floors, hallways, or outdoor locations, giving attackers opportunities to plug in malicious tools, extract data, or replace hardware unnoticed.
Supply chain risks
Vulnerabilities can be introduced during manufacturing, shipping, or integration by third-party vendors. A compromised device may appear normal while quietly providing hidden access.
Common cybersecurity risks for IoT ecosystems
IoT ecosystems face a mix of digital and physical threats that can jeopardize an entire network. Understanding the most common dangers helps you design stronger, more robust IoT ecosystems.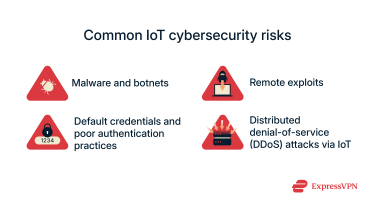
Malware and botnets
Malware is one of the fastest ways attackers take over IoT devices. Because these devices are almost always online and run minimal software, they’re easy targets. Once malware gets into an IoT device, the attacker can steal data from it or add it to a larger pool of infected devices.
That pool is called a botnet. IoT botnets are built from thousands of compromised IoT devices that can generate enormous traffic and support large, coordinated attacks. The Mirai botnet is the classic example: it compromised insecure cameras and routers and used them collectively to overwhelm major websites.
Remote exploits
Attackers often look for ways to access IoT devices over the network without ever being physically near them. Unpatched vulnerabilities, exposed services, and weak interfaces make this possible. Once they find a path in, they can execute code, change settings, or take complete control of the device.
In many cases, remote exploitation is made even easier by insecure communication channels. When devices rely on outdated or unencrypted protocols, attackers who can observe or tamper with the traffic may be able to steal or forge the information the device uses to decide who is allowed in. That matters because the features exposed to the outside world are usually limited and well-secured.
But once someone appears to be an authenticated or trusted user, the device exposes a much larger set of internal functions. This broader internal surface is harder to secure thoroughly and often receives less scrutiny from developers, who assume only legitimate users will ever reach it. If an attacker reaches that wider surface, the odds of finding serious vulnerabilities increase dramatically. From there, they can often achieve complete code execution on the device, run their own programs, maintain persistence, and move deeper into the network.
Default credentials and poor authentication practices
Weak authentication is one of the most preventable, but still one of the most common, IoT security issues. Many devices ship with factory-set usernames and passwords, and not every deployment changes them during setup. Others lack support for modern authentication methods, like unique device credentials, certificates, or two-factor (2FA) authentication.
Attackers exploit this by using automated scanners that search the internet for devices still using default credentials. Once they find one, they can easily break in.
Distributed denial-of-service (DDoS) attacks via IoT
IoT devices have become a favored tool for DoS or DDoS attacks because compromised devices can be coordinated to generate vast amounts of traffic. Even low-power devices, when grouped in large numbers, can overwhelm websites, online services, or corporate networks. Attackers often use botnets to control thousands of IoT devices simultaneously, flooding targets with requests until the system becomes unavailable.
The real strength of these attacks comes from their distribution. A small number of powerful machines is relatively easy to spot and filter out because their traffic stands out from that of regular users. But thousands of everyday IoT devices, each sending small amounts of traffic, blend in much more easily. That makes it difficult for defenders to tell malicious traffic apart from legitimate users, and any attempt to block it risks cutting off real customers as well.
The growing number of IoT devices worldwide has made these attacks more frequent and more powerful. Many devices aren't monitored closely, so owners may not realize their device is part of an active botnet. This makes IoT-driven DDoS attacks especially dangerous: they’re easy to launch, difficult to trace, and capable of causing widespread disruption.
Frameworks and standards for IoT cybersecurity
Here’s a quick summary of the IoT cybersecurity frameworks and standards:
| Framework/regulation | Scope | Key focus |
| National Institute of Standards and Technology (NIST) Cybersecurity Framework | Broad organizational cybersecurity | Practical, risk-based guidance to help organizations secure IoT systems and strengthen overall cyber resilience |
| Global System for Mobile Communications Association (GSMA) IoT Security Guidelines | Mobile and telecom IoT deployments | Best practices for securing connected devices throughout their lifecycle, including network segmentation and protection |
| Industry IoT Consortium (IIC) | Industry IoT (manufacturing, utilities, transport) | Structured model for assessing and improving IIoT security maturity across people, processes, and technologies |
| General Data Protection Regulation (GDPR) / Health Insurance Portability and Accountability Act (HIPAA) / Payment Card Industry Data Security Standard (PCI DSS) | Legal and compliance regulations | Protecting sensitive data and ensuring IoT environments meet strict privacy, security, and compliance requirements |
| International Organization for Standardization / International Electrotechnical Commission (ISO/IEC) 27001/IEC 62443 | Global information security and industrial systems | Standardized approaches for implementing, managing, and certifying robust information security and industrial control system protections |
NIST cybersecurity framework for IoT
The National Institute of Standards and Technology (NIST) IoT guidance states that all linked devices form a larger network. This means that no single security solution works for all situations.
Instead, NIST promotes a flexible, risk-based approach that allows organizations to select the appropriate protections for their devices and environments. That said, it recommends ensuring that IoT data is private, managing who can access it, keeping software up to date, and detecting dangers early. It also underscores the need for industry, government, and technology developers to work together to improve IoT device security across the board.
GSMA guidelines for secure IoT deployments
The Global System for Mobile Communications (GSMA) provides industry-specific guidance on keeping large-scale IoT deployments safe in mobile and telecom settings. These include offering a Coordinated Vulnerability Disclosure (CVD) scheme for researchers to report vulnerabilities and implementing a Trusted Computing Base (TCB) in both the IoT devices and the service ecosystem.
Industry IoT Consortium (IIC) Recommendations
The Industry IoT Consortium (IIC) focuses on the Industrial Internet of Things (IIoT) used in industrial and operational environments: places where connected devices directly affect equipment, safety, and uptime. Their recommendations help organizations bridge the gap between IT security and operational technology, which often have very different priorities.
They outline how to protect industrial endpoints, secure machine-to-machine communication, and integrate monitoring that fits environments where uptime and safety matter as much as data protection. It also publishes frameworks like the IoT Security Maturity Model (SMM), which help you measure how well your IoT security program supports your business in achieving its goals.
Compliance regulations (GDPR, HIPAA, PCI DSS)
Many IoT devices collect personal information, health data, or payment-related details, which brings them under many regulations, depending on the environment. These regulations influence how data is stored, transmitted, and processed throughout an IoT system. For example:
- General Data Protection Regulation (GDPR): Applies if your IoT device collects or processes personal data from EU residents.
- Health Insurance Portability and Accountability Act (HIPAA): Governs connected medical devices in the U.S.
- Payment Card Industry Data Security Standard (PCI DSS): Applies to IoT terminals, sensors, or gateways involved in payment flows.
You need to meet technical IoT standards, but you also need to follow data protection, audit, and privacy rules, especially when your devices operate across different jurisdictions.
Certification standards (ISO/IEC 27001, IEC 62443)
Certification standards offer structured ways to validate that IoT systems follow recognized security practices. International Organization for Standardization / International Electrotechnical Commission (ISO/IEC) 27001 provides a broad security management framework, which helps organizations control access, manage risks, and maintain policies across their entire environment.
IEC 62443 is more specialized, focusing on industrial automation and control systems. It outlines requirements for secure development, hardening, testing, and maintenance of industrial IoT components. These standards are helpful when organizations need assurance, internally or with partners, that their IoT systems meet a consistent, measurable security baseline.
Best practices for strengthening IoT cybersecurity
Strengthening IoT cybersecurity requires more than strong passwords; it calls for a layered, proactive strategy. The following best practices can help safeguard IoT environments from data breaches, unauthorized access, and emerging cyber threats.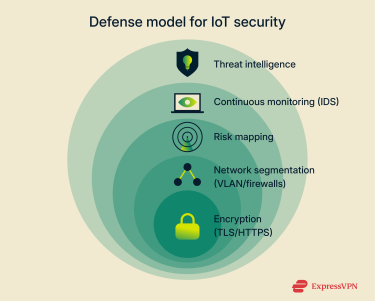
Encrypt communication using secure protocols (TLS, HTTPS)
Encryption is essential because IoT devices constantly send data across networks, sometimes locally, sometimes over the internet, and often to cloud platforms. Without encryption, anyone on the network path can intercept, read, or modify that data. Implementing protocols like Transport Layer Security (TLS) and Hypertext Transfer Protocol Secure (HTTPS) ensures that communication is both authenticated and protected against tampering.
For devices with limited resources, lightweight cryptography or hardware security modules can help maintain performance. The key is making sure encryption is applied consistently across devices, gateways, apps, APIs, and cloud services, so there are no weak links in the communication chain.
Segment IoT devices on separate networks (VLAN, Firewalls)
Segmentation matters for IoT because most devices don’t need to communicate with anything other than their controller or cloud service. When you put them on isolated networks, you can restrict them to exactly those destinations and block everything else. This stops a compromised device from reaching internal systems it has no reason to access.
You can do this with a virtual local area network (VLAN), which creates a dedicated network segment just for that group of devices. Once the devices are on their own VLAN, you can apply firewall rules to control exactly where their traffic is allowed to go.
For example, you might place all smart cameras on a single VLAN and then use firewall policies that only allow them to communicate with the video management server. If an attacker compromises a camera, they’re locked inside that VLAN and can’t jump to the rest of your network.
Risk mapping for IoT networks
Risk mapping involves identifying all IoT devices, how they connect, and what data or functions they support. This is important because not all devices carry the same level of risk: some only collect basic telemetry, while others control physical equipment or access sensitive systems.
By laying a visual map of your IoT network, you can see which devices have the biggest impact if they fail or are compromised, spot network weaknesses, and decide where stronger controls or isolation are needed. It helps you focus security efforts where they actually matter instead of spreading them evenly across every device.
Deploy continuous monitoring and intrusion detection
IoT devices rarely display clear signs when something goes wrong. Continuous monitoring fills that visibility gap by tracking device behavior, traffic patterns, and communication flows.
Tools like intrusion detection systems (IDS) and behavioral analytics can flag suspicious activity, and make it possible to contain issues before they escalate, especially in large or distributed environments where manually checking devices isn’t realistic.
Cybersecurity threat intelligence for IoT ecosystems
IoT-focused threat intelligence provides organizations with insight into the real-world threats targeting connected devices today. This includes new botnets, recently exploited vulnerabilities, attacker tools, firmware issues, and industry-specific risks.
Integrating threat intelligence into security operations helps teams:
- Prioritize patching based on active threats.
- Update firewall or detection rules before an attack hits.
- Understand which devices are most exposed.
- Anticipate emerging attack trends across IoT sectors.
Using VPNs to protect IoT communications
Note: Virtual private networks (VPNs) used in industrial and enterprise environments operate differently from consumer VPN apps. The sections below describe both types in their appropriate contexts: enterprise VPNs for securing large-scale or industrial IoT systems, and consumer VPNs (like ExpressVPN) for protecting smart home devices and personal networks.
VPNs (virtual private networks) enhance cloud security by creating a trusted, encrypted tunnel between IoT devices and cloud services. This helps protect sensitive information from eavesdroppers and allows authorized personnel to securely access cloud-hosted resources from anywhere.
How VPNs secure data in transit from IoT devices
A VPN creates a secure tunnel between IoT devices and their destination servers. In this tunnel, all data traveling between the IoT device and the server is encrypted, meaning that if anyone intercepts it, they’ll see only a string of symbols that don’t make sense. This prevents attackers from reading or manipulating data, like camera feeds and sensor data, as it travels across public or untrusted networks.
Site-to-site VPNs for industrial systems
In industrial settings, IoT devices often send data between different facilities, remote sites, or operational networks. Site-to-site VPNs remove the need to expose devices to the public internet. Without a VPN, a device at Site A must be reachable from Site B, which usually means opening it up to the outside world. A site-to-site VPN connects the two networks as if they were part of the same private subnet.
This protects Supervisory Control and Data Acquisition (SCADA) controllers, sensors, and industrial gateways that need to communicate over long distances. It also protects important operational data, even when that traffic has to travel across public networks.
VPN limitations for embedded IoT devices
VPNs can help keep data safe, but they don't necessarily work with every IoT device. Many embedded devices, such as sensors or small controllers, don't have the computing power or memory to run VPN software efficiently. In such situations, alternatives such as NIST’s lightweight cryptography standard can provide similar protection without overloading the device.
ExpressVPN as a consumer-level IoT safeguard
ExpressVPN is a practical solution for protecting your smart home from hackers. By installing it on a router, all Wi-Fi-connected IoT devices, such as cameras, thermostats, and voice assistants, automatically get encrypted connections. This arrangement secures all outbound IoT traffic, hides your home IP address, and reduces exposure to network-level attacks.
Building a cybersecurity strategy for IoT networks
Creating a strong IoT cybersecurity strategy requires careful planning, clear roles, and constant monitoring. The following practices can help you design a strategy that lowers risk, increases resilience, and ensures IoT security aligns with your overall business goals.
Building IoT cybersecurity teams and governance
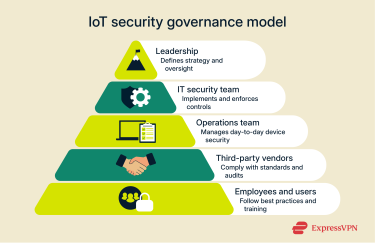 Effective IoT security starts with people and structure. You should either make separate cybersecurity teams or give defined IoT security tasks to people in your current IT departments. Good governance makes sure that everyone is accountable and that teams work together. Some important steps are:
Effective IoT security starts with people and structure. You should either make separate cybersecurity teams or give defined IoT security tasks to people in your current IT departments. Good governance makes sure that everyone is accountable and that teams work together. Some important steps are:
- Defining roles and responsibilities for managing IoT security.
- Setting clear policies for device use, access control, and data protection.
- Establishing communication channels between IT, operations, and leadership to coordinate responses to emerging threats.
Third-party vendor risk in large-scale IoT deployments
Large IoT deployments often depend on external vendors for hardware, software, and cloud services. Each vendor adds another point of exposure, which is why managing these dependencies is critical to keeping the overall system secure.
To control vendor risk:
- Check security policies before onboarding new vendors.
- Make sure they comply with industry standards, such as ISO 27001 or NIST guidelines.
- Regularly audit and review vendor performance and patch management.
Selecting enterprise-grade security tools
Not all security tools are designed for IoT. Enterprise-grade solutions offer broader protection, scale more effectively, and give you centralized control. They’re built to monitor large numbers of devices across complex networks and provide the visibility you need to stay ahead of threats. Look for tools that:
- Let you see what's going on with linked devices in real time.
- Integrate with existing systems, such as security information and event management (SIEM) platforms or cloud dashboards.
- Give automatic threat detection and response to minimize downtime.
Employee training on IoT attack vectors
Regular training helps employees recognize IoT-specific risks, such as insecure device configurations, unauthorized firmware updates, and attacks targeting connected systems. Effective training should:
- Teach best practices for securing connected devices.
- Use real examples of IoT attacks and how to avoid them.
- Build a security-first mindset so every employee contributes to overall protection.
Incident response planning for IoT breaches
When an IoT breach occurs, teams need to act quickly and follow a clear process. A solid incident response plan outlines how to contain the attack, investigate what happened, and restore affected systems. A good plan should:
- Define key response roles and communication steps.
- Provide precise steps for isolating compromised devices and restoring systems to service.
- Feed lessons learned into ongoing security improvements.
Testing the plan regularly makes sure that when a real incident happens, everyone knows their part.
FAQ: Common questions about IoT cybersecurity
What are the biggest threats facing IoT today?
The biggest threats to Internet of Things (IoT) devices and networks include weak authentication, unencrypted data transfers, outdated firmware, and a fast-growing attack surface. Attackers can exploit default passwords, misconfigured networks, and unpatched security holes.
What frameworks help protect IoT ecosystems?
Key frameworks that guide Internet of Things (IoT) security include the National Institute of Standards and Technology (NIST) Cybersecurity Framework and International Organization for Standardization / International Electrotechnical Commission (ISO/IEC) 27001. These standards help you identify risks, set controls, manage the device lifecycle, and ensure that vendors follow secure design practices.
What future technologies will shape IoT cybersecurity?
New technologies like artificial intelligence, machine learning, blockchain, and edge computing are changing how we protect Internet of Things (IoT) devices. These innovations make it easier to find threats, manage identities, and make decisions more quickly.
How do enterprise networks handle IoT access control?
Enterprise networks manage Internet of Things (IoT) access control by identifying devices, assigning unique credentials, segmenting traffic, and applying least-privilege policies. You can use centralized identity management systems to enforce who or what can access devices, limit what they can do, and watch for abnormal activity in real time.
What is the NIST approach to IoT cybersecurity?
The National Institute of Standards and Technology (NIST) approach to IoT cybersecurity is risk-based, ecosystem-aware, and outcome-driven. It suggests viewing IoT devices as part of a connected ecosystem, defining the security outcomes you want, and selecting controls based on your specific risk profile.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN