What are IoT networks? A complete guide

From smart homes to entire cities, connected devices now shape how we live and work. They collect data, share information instantly, and make everyday systems more efficient.
Behind that constant communication are Internet of Things (IoT) networks, the systems that connect devices, route data, and coordinate actions. These networks ensure that data flows reliably, securely, and in real time.
This guide explains how IoT networks function, why they’re important, and the challenges they face. It also includes information on how to keep your IoT network stable and secure.
Introduction to IoT networks
What is an IoT network?
An IoT network is the communication layer within the IoT ecosystem. It links physical devices like sensors, appliances, and machines to digital systems that analyze their data. Devices exchange data with these systems to stay in sync; that’s how thermostats self-adjust, smartwatches update, and sensors send instant alerts.
Why are IoT networks important?
IoT networks play a vital role in how technology supports daily life. They help systems react instantly and operate efficiently at scale, enabling:
- Better awareness: Real-time visibility across equipment and services.
- Faster decisions: Continuous data flow helps detect issues early and trigger responses before they escalate.
- Resource efficiency: Accurate data allows automatic adjustments to energy use, water flow, or maintenance schedules, cutting waste and cost.
- Improved safety: Ongoing monitoring detects risks early and safeguards people and assets in critical environments such as healthcare and transportation.
How do IoT networks work?
An IoT network manages how connected devices capture and transmit data and convert it into action. When a sensor measures something, like temperature or motion, the data travels through the network to be processed, stored, and used.
Key components of IoT networks
Every IoT network depends on core elements that link the physical world with digital infrastructure, each with a clear role to play.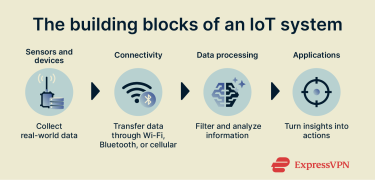
- Sensors and devices: The “things” in the Internet of Things measure conditions like temperature, motion, or light, and convert them into digital data for the network to use.
- Connectivity: Technologies such as Wi-Fi, Bluetooth, Zigbee, and cellular move data through gateways and routers to cloud systems.
- Data processing: At the edge, nearby devices filter and summarize information. In the cloud, deeper analysis identifies patterns, predicts events, and stores results.
- Applications and interfaces: This layer processes and presents data via dashboards and alerts. Applications may also take automated actions based upon the processed data.
How IoT devices communicate
Most networks use three main communication types:
- Device to Device: Devices connect directly without the internet. An example would be a smart switch signaling to a light via Bluetooth or Zigbee.
- Device to Cloud: Devices send data directly to cloud platforms for storage, processing, or control. For example, wearables might transmit heart rate data directly to the cloud.
- Device to Gateway: This is where devices communicate with a local gateway before data is transmitted to the cloud or processed locally. Examples include industrial IoT sensors that send data to a gateway for filtering, aggregation, or encryption before it goes to a cloud platform.
Protocols and data flow in IoT systems
IoT networks use lightweight protocols that balance data flow, power use, and security:
- Message Queuing Telemetry Transport (MQTT): A low-bandwidth option, useful for sending frequent, small bursts of sensor data to the cloud.
- Constrained Application Protocol (CoAP): Ideal when specific data readings are needed regularly from multiple devices.
- Data Distribution Service (DDS): Common in industrial and robotics settings, it supports reliable, real-time communication between any devices or systems on the network.
After data is collected, it travels through two layers before analysis or storage:
- Transport: The Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) protocol suites handle data transmission. UDP is preferred for constrained or battery-powered devices because it has lower overhead, while TCP is used for larger data volumes and when applications require a persistent connection and strong data integrity.
- Security: Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) encrypt data to protect its privacy and integrity while it travels across public networks. TLS is used for TCP, while DTLS provides similar protection for UDP.
Types of IoT networks explained
The types of connections between devices in an IoT network can vary based on distance, power needs, and data volume.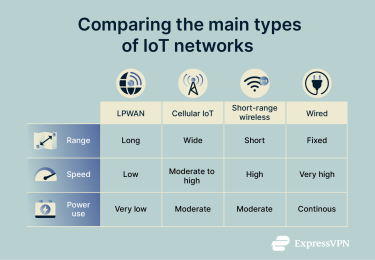
Low-power wide area networks (LPWAN)
LPWANs trade speed for efficiency, sending tiny messages over long distances while consuming so little power that devices can operate for years on a single battery. Examples include:
- Sigfox: A global network built for simplicity and energy conservation. Devices send short messages to base stations, keeping costs and power demands low; ideal for smart meters, asset tracking, and basic monitoring.
- Long-range wide area network (LoRaWAN): A publicly available, flexible LPWAN standard. Its Adaptive Data Rate feature balances range and energy use, making it suited for large-scale deployments like agriculture or environmental monitoring.
Cellular IoT
Built on mobile networks, cellular IoT connects devices using the same infrastructure as smartphones but with far lower energy demands. Performance is also optimized for sensors and machines.
This is useful for connected systems that need constant, reliable communication while on the move, or those that operate in remote areas with no local infrastructure. Think of a forest-wide sensor network to detect wildfires that uses only battery-powered nodes and small solar panels.
In these environments, most communication methods become unfeasible, and cellular IoT may be the only practical option. While poor signal is an issue in remote areas, implementing high-quality shielded antennas and several layers of redundancies can help ensure reliable communication.
There are two main cellular IoT standards:
Long-Term Evolution for Machines (LTE-M): Designed for devices that need faster data transfers and mobility, such as wearables, vehicle trackers, or payment terminals. It supports voice calls and smooth handover between cell towers, keeping moving devices connected.
Narrowband IoT (NB IoT): Built for simplicity and deep coverage. It’s slower than LTE-M but more efficient for fixed sensors sending small data packets, like water meters or environmental monitors in remote or underground areas.
Both standards operate within the global 4G and 5G networks, offering wide coverage, reliability, and easy integration with existing infrastructure.
Short range wireless networks
Not all IoT connections need long-distance communication. Short-range networks connect devices within the same home or workspace, where speed and responsiveness matter more than range. They include:
- Zigbee: A low-power wireless standard used in smart homes. It creates a mesh network where devices relay messages to each other, keeping communication stable even if one goes offline; ideal for lighting, temperature control, and energy management.
- Bluetooth Low Energy (BLE): Sends small data bursts while conserving battery life. It powers wearables, trackers, and beacons, and connects easily with smartphones and tablets.
- Wi-Fi: Delivers the highest data transfer speeds for cameras, appliances, assistants, and similar products. Though it uses more power, Wi-Fi offers the stability and bandwidth needed for real-time applications.
- Ultra-wideband: While more expensive and specialized than Wi-Fi, Bluetooth, or standard LPWANs, it measures the time it takes for radio pulses to travel between devices, offering extremely precise location tracking.
Wired IoT networks
For critical industrial IoT systems, wired networks remain the backbone, trading flexibility for guaranteed stability. Wired IoT networks can deliver:
- Reliability: Cables avoid dropouts and interference, keeping systems in factories, hospitals, and control rooms running without delay.
- Security: Data stays within a closed physical line, making interception less likely; ideal for sensitive or proprietary operations.
- Power and simplicity: Power over Ethernet (PoE) supplies both power and data through one cable, cutting clutter and installation costs.
IoT network architecture: Layers and structure
Every IoT layer within a strong IoT infrastructure handles a specific task, so devices, networks, and platforms can work securely and efficiently together.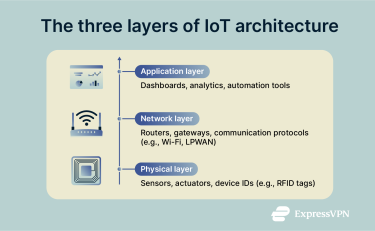
Application layer
At the top of the IoT structure is the application layer, where raw data is transformed into useful information. Software platforms and analytics tools process data to generate insights or perform actions.
It has two main roles:
- Analysis: Interpreting data to highlight patterns or issues, like spotting unusual energy use or predicting when a machine might need maintenance.
- Interaction: Connecting people and systems through dashboards or automated responses, sending commands back to devices or feeding information into business tools such as inventory or asset management systems.
Network layer
This layer acts as the communication backbone of an IoT system. Its role is to move data securely and reliably from the physical devices to where it will be processed, whether that’s in the cloud or on a local server.
It’s here that all the connection rules and transport methods come into play: devices connect through technologies such as LPWAN, cellular, or Wi-Fi, while protocols like IPv6 and specialized routing schemes, such as Routing Protocol for Low-Power and Lossy Networks (RPL), determine the most efficient path for each data packet.
Physical layer
The physical layer is where every IoT system begins. It includes sensors that collect data like temperature or motion and actuators that turn digital commands into actions, such as opening a valve or switching on a light.
Edge vs. cloud architecture in IoT
In IoT systems, where data is processed matters as much as how it’s collected. Cloud computing sends data to remote servers for analysis and storage. It offers massive capacity and computing power, with strong IoT cloud security protecting information in transit and at rest. However, it depends on a stable connection and there may be delay due to factors like network latency and bandwidth limitations.
Edge computing processes data closer to the source on local devices or gateways, reducing latency, enabling real-time decisions, and limiting what needs to be sent to the cloud.
Most IoT systems use both: the edge for instant responses and the cloud for deeper analysis.
Securing IoT networks: Best practices
Securing IoT networks means protecting countless connected devices that share data continuously. A single weak link can expose the whole system, so security must be built into every layer. Strong IoT cybersecurity practices protect devices, data, and communication channels while improving privacy, integrity, and network resilience.
Secure data transmission
When data moves through an IoT network, from local sensors to gateways or the public internet, it must stay protected at every step. Securing data in transit prevents interception, tampering, or unauthorized access.
- Encrypt data from start to finish: Encrypt information before it leaves the device and decrypt it only at its destination. Use TLS for devices and applications that rely on TCP, and DTLS for those based on UDP.
- Make sure nothing changes in transit: Integrity checks confirm that received data matches what was sent, using cryptographic hashes and message authentication codes (MACs) to detect tampering or hidden changes.
- Handle certificates and keys carefully: Digital certificates verify device identities and enable encryption. Keep them current, revoke when needed, and store them securely.
- Maintain a reliable chain of trust: Secure communication only works if devices trust the right certificate authorities. In IoT, updating and managing these trusted roots can be challenging. Tools that manage certificate issuance, rotation, and revocation across all devices can help keep the chain of trust intact.
Strong access controls
Controlling who or what can access your IoT network helps stop security issues before they spread. Each user, app, or device should only perform its intended role.
- Limit permissions: Operate on a zero-trust model, giving each device or user only the minimum access required to perform its role or function.
- Use roles: Group devices and users into roles, like sensor, admin, or viewer, for easier, safer management.
- Verify identity: Use digital certificates for devices and strong multi-factor authentication (MFA) for users. Always change default credentials.
- Segment networks: Keep IoT devices on a separate network from critical systems to contain any breaches.
- Monitor activity: Log and review connections regularly to spot unusual behavior early.
Device authentication and firmware updates
IoT devices need to stay secure for their entire lifespan. Each one must have a trusted identity and a safe way to receive updates.
A secure chip in the device, known as a hardware root of trust, can store cryptographic keys and prevent cloning or tampering. And when devices connect, they use digital certificates, not passwords, to prove who they are. This method, called public key infrastructure (PKI), ensures both sides verify each other before sharing data.
Updates follow the same rule of trust. Firmware should arrive encrypted and digitally signed, and the device must verify that signature before installation. If something goes wrong, a rollback system can restore the previous version automatically.
Using VPNs with IoT devices: Privacy and protection
Connected devices make life easier, but every connection can also open a door. Many IoT devices share data without strong safeguards, exposing information and creating weak points. Securing your network, whether at home, in an office, or across a wider system, is essential to keep these devices protected.
How consumer VPNs protect IoT traffic
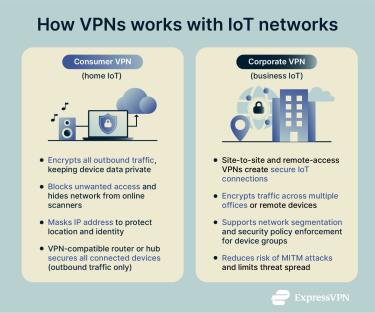 A consumer virtual private network (VPN) creates a private, encrypted tunnel for your entire home network. It can:
A consumer virtual private network (VPN) creates a private, encrypted tunnel for your entire home network. It can:
- Keep data private: Many smart devices send information in plain text, making it easy to intercept. A VPN encrypts all this traffic, so it stays private and hidden from your internet service provider (ISP) and other third parties. Anyone trying to intercept it will only see scrambled code.
- Block unwanted access: Without a VPN, your devices and network can be visible to online scanners, making them easier targets for attack.
- Mask your network’s identity: The VPN replaces your real IP address with its own, keeping your location hidden and making it harder for threat actors to find or target your network.
VPN-compatible routers and smart hubs
Many smart devices can’t run VPN software themselves, so to protect them you’ll need a VPN-compatible router or a smart hub (a central device that manages and connects your IoT network). Installing a VPN on your router or hub creates a single, secure entry point for your network, protecting every connected device automatically.
Alternatively, you could choose a router with built-in VPN protection. ExpressVPN’s Aircove router, a Wi-Fi 6 device that delivers automatic encrypted coverage for your whole network. Using a VPN-compatible router or smart hub is a simple way to extend privacy and security to every connected device.
VPN vs. network segmentation
A VPN keeps outbound traffic private, but it can’t stop threats that are already inside your network. If a connected device becomes compromised, the risk can quickly spread.
Network segmentation prevents that from happening. It separates your Wi-Fi into different zones; for example, one for personal devices, another for work, and one just for smart home gadgets. Each group stays isolated, so if something goes wrong in one zone, the rest of your network remains secure.
Common consumer pitfalls
A VPN is a strong privacy tool, but it’s not a silver bullet for IoT security. There are a few common issues that come up:
- Compatibility problems: Some older or low-cost IoT devices struggle to work with certain VPN protocols, causing unstable connections or forcing users to disable encryption for specific devices.
- Slower performance: Routing all data through a VPN can strain your router’s resources. Smart cameras or gaming systems that depend on quick responses may experience some delays.
- Cloud service conflicts: Many IoT products depend on the manufacturer’s servers to function. If your VPN connects through another region, some devices may fail to sync or lose access.
Troubleshooting tips: Check if your device supports the VPN protocol you’re using, and change protocol if necessary. Also, consider splitting your traffic so only sensitive devices go through the VPN connection. Finally, if performance slows or cloud services fail, try connecting to a server that’s geographically closer to your location.
Corporate VPNs and IoT security
In a business context, VPNs secure IoT traffic across multiple locations and remote users. This can be via site-to-site VPNs that connect multiple offices or facilities securely, allowing IoT devices to communicate across locations. It can also be via remote-access VPNs, which enable employees or field devices like industrial sensors or vehicle trackers to access the corporate network safely.
Corporate VPNs offer strong protection against network-level IoT attacks by encrypting traffic. Specifically, this encryption reduces the risk from man-in-the-middle (MITM) attacks, where a threat actor tries to intercept and tamper with data shared between IoT devices.
Organizations can also use VPNs to divide IoT devices into separate private networks, facilitating the enforcement of specific security policies for device groups and containing potential threats within defined network zones.
Real-world applications of IoT networks
Smart homes and consumer IoT
Smart home technology brings convenience, control, and energy savings to everyday life. Connected devices, like cameras, thermostats, and voice assistants, work together through the home’s IoT network to automate routines and respond in real time. They can adjust lighting and temperature, send security alerts, or let you check on your home remotely from your phone.
Industrial IoT (IIoT)
Industrial IoT (IIoT) powers efficiency, safety, and precision. Sensors and connected systems track equipment performance, energy use, and production in real time, helping companies prevent failures and cut downtime. Factories, energy plants, and logistics networks also use this data to predict maintenance and track assets across complex environments.
The main challenge is securing and integrating new IoT systems with older equipment not designed for connectivity or modern cybersecurity. Errors, inaccurate data, or tampering can directly impact employee safety and operational reliability.
Healthcare and medical devices
The Internet of Medical Things (IoMT) is a network of connected medical devices and sensors that collect and share health information. These systems are used in hospitals, clinics, and homes to track vital signs, locate medical equipment, and support remote consultations.
Because they handle sensitive patient data, IoMT devices must comply with strict privacy laws in different regions, such as the Health Insurance Portability and Accountability Act (HIPAA) in the U.S. and the General Data Protection Regulation (GDPR) in Europe. They also need strong safeguards to ensure accuracy and prevent tampering, since any error or breach can directly affect patient safety.
Smart cities and infrastructure
Cities are becoming smarter, with sensors and connected systems managing traffic, energy, and public services in real time. Smart traffic lights reduce congestion, while connected infrastructure monitors roads, bridges, and power grids to address issues before they progress.
IoT public safety systems play a central role by supporting emergency response, environmental monitoring, and critical infrastructure management. But as connectivity expands, cities must guard against cyberattacks and protect citizens’ privacy. Strong security and clear data policies help maintain safety and trust.
Challenges of IoT networks
- Lack of standardization: With so many manufacturers using their own communication methods, IoT devices don’t always speak the same language. This lack of shared standards can make it difficult to connect systems smoothly or manage them as one network. It can also lead to uneven security and lock users into closed ecosystems.
- Data management challenges: Connected devices generate massive amounts of data in different formats. Before that data can be used, it has to be cleaned, stored, and processed, often across multiple systems that don’t easily integrate. Without consistent structures or scalable tools, organizations can end up with fragmented data silos and delayed insights instead of the fast, automated decision-making IoT is meant to enable.
- Cybersecurity and privacy risks: Every new device is another door into the network. Weak passwords, outdated firmware, and inadequate safeguards can make devices easy targets. These common IoT vulnerabilities can expose entire networks to cyberattacks or data breaches if not properly addressed. Some IoT attacks target devices that collect sensitive personal information, such as location or usage patterns; it’s critical that such devices are properly protected.
How to design and deploy an IoT network
Given the challenges and risks of a poorly managed IoT network, it’s vital to thoroughly consider your options during the initial setup. Here are some key aspects to consider.
Choosing the right network type for your use case
Before connecting your devices, decide what matters most: distance, data speed, or battery life. That choice defines the type of network you need.
- Long-range, low-power networks: Best for sensors in remote areas like farms or pipelines. With this network type, devices can last years on a single battery.
- Cellular connections (like 4G or 5G): Perfect for mobile or high-bandwidth tasks such as vehicle tracking or live camera feeds. They’re reliable, but they use more power and cost more to run.
- Wi-Fi and Bluetooth: Ideal for homes or offices where devices are close together. Wi-Fi handles large data like video; Bluetooth is great for low-energy updates like temperature readings.
- Ultra-Wideband (UWB): This is a good choice for applications that require precise device location data where GPS isn’t feasible. It can be used for asset tracking or indoor navigation, for example.
Planning device connectivity and coverage
Once you’ve chosen the connection type, you need a layout that keeps everything linked and stable. Most IoT systems use a hub or gateway that gathers data from devices and sends it to the cloud. Some setups connect every device directly to this hub, while others create a mesh network, where devices share signals with one another to extend range and reliability.
Selecting protocols and gateways
Your gateway is the bridge between your devices and the wider internet. It helps translate signals into a single, unified system and can process data locally before sending it to the cloud. Gateways come in many forms, from dedicated devices for industrial networks to smart home hubs and routers with built-in gateway functions.
Whichever system you choose, make sure it supports strong encryption and secure device identification so data stays private. Using a VPN can protect data as it travels across networks, ensuring devices communicate safely even across public or untrusted connections.
Managing power consumption and latency
For IoT networks that require timely data, minimizing latency is crucial. Placing gateways near devices, using edge computing, and selecting low-latency protocols can ensure faster responses. Mesh networks can extend coverage and reduce power needs for distant nodes, but may introduce latency as data hops between devices.
Direct hub connections use more energy for remote devices but provide lower latency. Balancing speed with power use ensures devices remain efficient without compromising real-time performance.
FAQ: Common questions about IoT networks
What are the 4 main types of IoT networks?
The four main types of Internet of Things (IoT) networks are Low Power Wide Area Networks (LPWAN), cellular IoT, short-range wireless networks, and wired IoT networks.
How does an IoT network work at home?
At home, an Internet of Things (IoT) network connects smart devices like lights, cameras, and thermostats through a router or hub that then sends data to the cloud. This data can be used to automate certain actions, and users may also be able to use the cloud to send remote commands to their IoT devices.
What is an IoT device on my Wi-Fi?
An Internet of Things (IoT) device on your Wi-Fi is any smart gadget that connects to your home network, such as a smart TV, voice assistant, or security camera. It uses short-range wireless networks to send and receive data.
What are the risks of IoT networks?
The main risks include weak security, inconsistent standards, and poor data management. Vulnerable devices or outdated firmware can expose networks to cyberattacks or data breaches.
Should I enable the IoT feature on my router?
Enable it if the feature creates a separate network for Internet of Things (IoT) devices. That isolation, known as network segmentation, is what actually protects your other devices. If the feature doesn’t provide this separation, it doesn’t help with security, so you can safely leave it off.
What is the future of IoT network technology?
Internet of Things (IoT) networks are moving toward faster, smarter, and more secure systems powered by 5G, edge AI, and stronger security standards. These advances will enable real-time automation, local data processing for quicker decisions, and more reliable protection of devices and information in homes, cities, and industries.
How is data protected in IoT systems?
Internet of Things (IoT) systems protect data through encryption, secure communication protocols, access controls, and digitally signed firmware updates. These measures keep information private and prevent unauthorized access.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN