Privacy vs. anonymity: Definitions, differences, and why it matters



Have you ever heard people use “privacy” and “anonymity” like they mean the same thing? They don’t. Privacy is about keeping your personal life to yourself, while anonymity is about hiding who you are altogether. Both matter online, but in very different ways.
In this article, we’ll explain the difference between privacy and anonymity, what they really mean, how they overlap, and why understanding that can change how you protect yourself online.
What is privacy?
Privacy is essentially about control: the ability to decide who gets access to your personal information and how it’s used. It’s not about hiding from the world but about having the freedom to share what you want on your own terms. There can be different types of privacy, but it generally means deciding how much of your life (your browsing habits, messages, location, or even your online purchases) others can see or use.
Digital privacy has become a huge part of our everyday lives because so much of what we do leaves behind a trail of personal data. Whether you’re checking your bank account, messaging a friend, or streaming a movie, you’re generating information that someone else could, in theory, access or exploit. Digital privacy gives you a way to put up boundaries so your personal life isn’t up for grabs by whoever happens to be watching.
Key elements of digital privacy
Digital privacy typically consists of 3 main elements, including the following:
- Individual privacy: This is about protecting information that directly identifies you, like your name, address, health records, tax details, or anything else that could be tied back to you personally. Keeping this information safe prevents things like identity theft or unauthorized profiling.
- Information privacy: Focuses on how organizations handle the data they collect about you: how it’s gathered, stored, and shared, and whether it’s done ethically and in compliance with laws like the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA).
- Communication privacy: This covers the security and confidentiality of your private conversations, like phone calls, texts, emails, or instant messages, ensuring that only you and your intended recipients can read or hear them.
Real-world examples
Digital privacy isn’t just a tech issue; it affects you in practical, personal ways every single day:
- Healthcare records: Your medical history, prescriptions, and lab results are confidential for a reason. If leaked, this sensitive data could be used to discriminate against or exploit you.
- Banking and shopping: Financial transactions contain highly sensitive details about your spending, income, and habits, all of which could be misused if exposed.
- Private conversations: Whether it’s an encrypted personal message to a partner or a private work email, you expect these exchanges to stay between the people involved, not to be scanned, stored, or sold.
- Web browsing: Even something as simple as what you search online can paint a detailed picture of your habits, preferences, and even vulnerabilities, which is why many people choose tools like virtual private networks (VPNs) or privacy-focused browsers to keep this information out of the wrong hands.
What is anonymity?
Anonymity means separating what you do from who you are. When you’re anonymous online, your activity (whether it’s browsing, commenting, or sharing information) can’t easily be linked back to your real-world identity. This means keeping personal details like your name, location, email address, or other identifiers separate from your actions.
Online anonymity often relies on tools like pseudonyms, VPNs, proxy servers, or privacy networks such as Tor to help obscure your identity. But it’s worth noting: true anonymity is difficult to achieve. Most digital interactions leave some kind of trace, and advanced tracking methods can often link patterns of behavior back to an individual, even without explicit identifiers.
Key traits of anonymity
Anonymity means your actions can’t easily be traced back to you, and it’s built on a few key principles:
- Non-identifiable: Nothing about your actions or data should reveal who you are, like your real name, address, or other personal details.
- Unreachable: No one should be able to use what you do online to contact or target you directly
- Untrackable: Your online activity shouldn’t be easily pieced together to trace back to your real-world identity.
Common use cases
An anonymous identity can be empowering. It allows people to speak freely, explore sensitive topics, or share important information without fear of judgment or retaliation. Some common situations where anonymity plays a critical role include:
- Journalism: Investigative journalists often rely on confidential sources to uncover corruption, human rights abuses, or government misconduct. Protecting these sources' anonymity is crucial for them to provide the necessary information without fear of retaliation.
- Whistleblowing: Individuals who expose illegal or unethical activities within organizations often face severe consequences. Whistleblowers benefit greatly from anonymity, enabling them to reveal crucial information that might otherwise remain hidden.
- Activism: In many parts of the world, activists advocating for human rights, environmental protection, or political change face surveillance and persecution. Anonymity allows them to organize, communicate, and express dissent safely.
- Online discussions: Many users prefer anonymity to discuss personal experiences or controversial opinions without being tied to their real name or job.
However, anonymity has a double edge. It can encourage honest dialogue and protect vulnerable voices, but it also opens the door to less positive behaviors, like trolling, harassment, or illegal activity, because some people feel less accountable when their identity is hidden.
That’s why debates about anonymity online are often complex: it’s both a shield for free expression and, at times, a tool for harm.
Privacy vs. anonymity vs. confidentiality: What’s the difference?
While often used interchangeably, privacy, anonymity, and confidentiality represent distinct yet interconnected concepts in data protection. We've explored privacy as control over personal data and anonymity as being unidentifiable. Now, let's introduce confidentiality.
Confidentiality is restricting access to information that has been voluntarily shared, ensuring it remains known to authorized parties only. For instance, the attorney-client privilege is a relationship built on confidentiality, where lawyers are meant to keep details shared by their client confidential.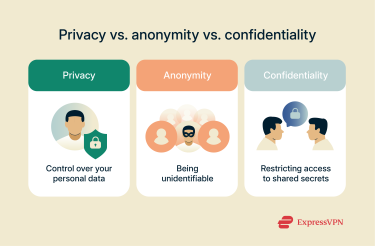 The following table elaborates how these three concepts compare:
The following table elaborates how these three concepts compare:
| Privacy | Anonymity | Confidentiality | |
| Purpose | Control over personal information | Prevent identity linkage to actions/data | Ensure shared information remains secret |
| Use | Broadly applies to personal data control | Used when hiding identity is paramount, such as whistleblowing | Agreement between parties on shared data |
| Scope | An individual's right to control personal information | Absence of personal identification | Protecting specific information from unauthorized disclosure |
Complementary vs. conflicting roles
Privacy, anonymity, and confidentiality often work together, but not always. Sometimes they strengthen each other, and other times they clash, depending on how they’re applied.
How they complement each other
- Confidentiality supports privacy: When an organization promises confidentiality, it means any personal information you share stays protected and isn’t exposed to unauthorized parties. This directly helps maintain your privacy.
- Anonymity enhances privacy: Stripping away identifying details makes it harder for anyone to link data back to you. Even if your activity is visible, anonymity helps keep it private by disconnecting it from your personal identity.
Where they can conflict
- Confidentiality vs. anonymity: Information might be kept confidential (accessible only to authorized people) but still linked directly to your identity. For example, your medical records are private and confidential, yet they clearly identify you.
- Privacy vs. anonymity: Privacy means your conversations or data are protected from outsiders (like encrypted chats), but they can still be linked to you through metadata, like who you talked to and when. Anonymity focuses on hiding your identity, so even if metadata exists, it’s harder to trace it back to you personally.
Legal implications of privacy vs. anonymity
Laws around the world are evolving quickly to keep up with concerns about how personal data is collected, used, and protected online. Most of these laws focus on privacy, giving people control over their personal information, rather than on guaranteeing full anonymity.
For example, under the EU’s General Data Protection Regulation (GDPR), fully anonymous data falls outside its scope because it can’t be linked back to a person. However, the GDPR allows for pseudonymization, which reduces how much personal information is exposed and limits identifiability.
In the U.S., the California Consumer Privacy Act (CCPA) gives residents rights to know what personal information companies collect about them, how it’s used, and who it’s shared with. It also gives them the right to delete certain data and limit how businesses handle sensitive information. While the CCPA strengthens privacy protections, it doesn’t specifically address anonymity.
Notable legal cases and enforcement examples
Several recent cases and regulatory actions highlight how courts and authorities balance privacy, anonymity, and personal data rights:
- Prismall v Google/DeepMind: This case involved the transfer of 1.6 million National Health Service (NHS) patient records to DeepMind (a Google-owned AI company) to develop a medical tool, without explicit patient consent. The court ultimately dismissed the claim, ruling there wasn’t enough evidence that private information had been misused.
- WFZ v BBC: A man sought to block the BBC from naming him in connection with uncharged criminal allegations. The High Court ruled in his favor, noting that individuals have a reasonable expectation of privacy. The case shows how courts can grant anonymity in legal proceedings when disclosure could unfairly damage someone’s reputation.
- Yahoo! France cookie consent fine: France’s data protection authority fined Yahoo! €10 million for placing cookies on user devices without informed consent and making opting out unnecessarily difficult. The case reinforced the importance of clear consent and highlighted ongoing tensions between anonymous web tracking and user privacy rights.
- Tele2 Sverige, Watson, and others: The European Court of Justice ruled that laws requiring blanket retention (storing traffic and location data from all users by default, regardless of suspicion) violate EU privacy and data protection rights. It allowed only targeted retention for serious crime, with strict limits, court or independent oversight, and safeguards like EU-based data storage.
Challenges to privacy and anonymity
The internet’s interconnected nature, combined with powerful tools for data collection and analysis, has made personal information more vulnerable than ever. Both deliberate surveillance and accidental leaks can put your digital identity at risk.
Government surveillance and corporate data collection
Many governments engage in mass or targeted surveillance, intercepting communications and collecting vast amounts of data on their citizens. This practice is often justified by national security but can infringe upon human rights, including privacy and freedom of expression. Such surveillance can deter individuals from expressing opinions freely.
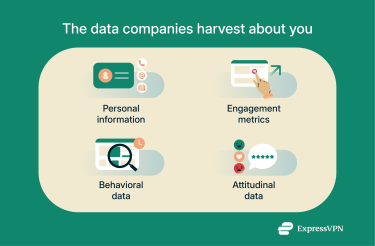
Companies are also major players in data collection, gathering information for targeted advertising, product development, or even selling to third parties. Every click, search, and purchase can be logged and analyzed, often without people realizing just how much is being tracked. This data can include:
- Personal information: Basic details like your name, phone number, date of birth, gender, IP address, and device IDs
- Engagement metrics: How you interact with online content, such as social media likes, ad clicks, emails opened, or app usage patterns
- Behavioral data: How often you use a product, which features you prefer, and how long you stay on certain pages
- Attitudinal data: Insights into your preferences and opinions, like product satisfaction ratings or purchase motivations
Learn more: Beyond the largest companies, even your internet service provider (ISP) can collect vast amounts of personal information. Check out the best ways to hide your browsing history.
User errors and misconceptions
Many privacy and anonymity risks don’t come from hackers or surveillance programs but from users themselves, often through simple mistakes or misunderstandings. Here are some common pitfalls:
- Weak and reused passwords: Simple or repeated passwords make accounts easy targets for attackers. A password manager can help create and store strong, unique passwords for every account.
- Oversharing on social media: Posting personal details, like your home address, daily routine, or vacation plans, can open the door to identity theft or other malicious activity.
- Skipping privacy policies: It’s tempting to click “I agree” without reading, but doing so often means unknowingly allowing extensive data collection and sharing.
- Using unsecured Wi-Fi: Public Wi‑Fi networks can expose your online activity to snooping or interception. Learn how to stay safe on public Wi-Fi so your sensitive information isn’t compromised.
How technology can weaken anonymity
While technology offers tools for protection, its advancements can also undermine anonymity in the following ways:
- Sophisticated tracking: The evolution of advanced tracking techniques like browser fingerprinting and metadata collection makes it increasingly difficult to remain untrackable online.
- Big data analytics and AI: The ability to process and analyze vast datasets combined with AI allows for highly accurate profiling and even de-anonymization of individuals from seemingly anonymous data.
- Facial recognition and biometrics: Facial recognition technology and other biometric data collection erode anonymity and make it easier to identify individuals without their consent.
- Internet of Things (IoT) devices: The growing number of IoT devices, from smart home assistants to wearable tech, constantly collect data on user behavior, location, and even health, creating a surveillance network.
Popular tools for protecting privacy and anonymity
There are plenty of tools to help you protect your identity and control your digital footprint. While no single solution makes you completely invisible, using the right mix of tools can significantly improve your online security. Some of these tools focus on privacy (controlling who sees your data), others focus on anonymity (hiding who you are), and a few do both.
Privacy-focused tools
These tools help limit the amount of personal information you share online:
- Virtual private network (VPN): A quality VPN like ExpressVPN hides your IP address and encrypts your internet traffic, creating a secure tunnel between you and the web. This helps protect your privacy and can also support your anonymity by making it harder to trace your online activity.
- Private search engines: There are various private search engines that provide search results without creating a personalized profile of your interests, thus protecting your privacy.
- Encrypted messaging apps: Secure messaging apps with end-to-end encryption ensure only the sender and recipient can read messages, helping protect the confidentiality of your communications.
- Ad blockers: These tools don’t just stop annoying ads from cluttering your screen; they also block many third‑party trackers that monitor your browsing habits. ExpressVPN includes a built‑in ad and tracker blocker for extra privacy.
- Private web browsers: Consider switching to a private web browser that gives you more control over what information you share online.
Anonymity-focused tools
These tools make it harder to link your actions to your real-world identity. However, no tool can guarantee complete privacy or anonymity, so it’s important to combine them with safe online habits.
- The Onion Router (Tor): Tor routes your internet traffic through a volunteer network of relays, encrypting it multiple times and making it extremely difficult to trace the traffic back to its origin. Using Tor with a VPN can add an extra layer of anonymity.
- Disposable email addresses: Temporary email addresses let you sign up for services without exposing your personal email, reducing the chance of it being linked back to you.
- Cryptocurrency: Most cryptocurrency is pseudonymous, not fully anonymous, because transactions are recorded on a public ledger. However, privacy-focused coins (like Monero) or tools like cryptocurrency mixers can increase anonymity where permitted by law.
The role of privacy and anonymity in public life
Privacy and anonymity are cornerstones of a healthy democracy. They allow people to speak freely, report wrongdoing, and seek out information without fear of retaliation.
At the same time, these rights create a complex balancing act between protecting individual freedoms and meeting society’s needs for transparency and safety. Getting this balance right is essential for an open, fair society that also respects personal liberties.
Balancing transparency and freedom
Privacy and anonymity have clear benefits, but absolute application can sometimes clash with the public interest. Here are a few examples where the impact can go both ways:
- Freedom of expression: Anonymity helps people speak their minds without fear of backlash, but it can also enable harassment, hate speech, and the spread of misinformation.
- Law enforcement and national security: Law enforcement agencies often argue that increased privacy and anonymity hinder their ability to investigate crimes, combat terrorism, or protect national security.
- Workplace feedback: Anonymous employee feedback systems encourage honesty but can create challenges in verifying claims or resolving specific issues.
- Politics: Anonymous voting protects democracy and prevents voter intimidation, yet anonymity online can fuel disinformation campaigns and even foreign election interference.
- Research: Ensuring privacy and anonymity in studies encourages honest participation, especially on sensitive topics, but it can limit researchers’ ability to verify data accuracy.
Final thoughts on privacy vs. anonymity
Privacy and anonymity are related but distinct concepts, and understanding the difference is crucial in today’s connected world. Privacy is about controlling who can access your personal information, while anonymity is about acting without being identified. Both are valuable, but they serve different purposes and require different tools and strategies to maintain.
Choosing the right approach for your digital life
How much privacy or anonymity you need depends on your goals and online activities:
- Assess your needs: Decide what information you want to protect and from whom. Are you mainly trying to avoid targeted ads (privacy), or do you need to share sensitive information without revealing who you are (anonymity)?
- Be mindful of context: Different situations call for different levels of protection. Posting on social media isn’t as sensitive as online banking, and whistleblowing requires a much higher level of anonymity.
- Layer your defenses: Use a mix of tools for better protection. A VPN can secure your connection, a privacy‑focused browser can limit tracking, and Tor can add an extra layer of anonymity when needed.
- Understand trade-offs: Strong privacy or anonymity often means sacrificing convenience. Know where you’re willing to compromise.
Staying informed as the landscape evolves
The digital landscape is constantly changing, with new technologies and regulations emerging regularly. It is crucial to stay informed by following developments in data privacy laws, security breaches, and new tracking technologies. Knowledge is your strongest defense against evolving threats.
Regularly review the privacy settings on your social media accounts, apps, and operating systems, as default settings are rarely the most privacy-focused. And learn how the privacy and anonymity tools you use actually work, so you understand both their strengths and their limitations.
FAQ: Common questions about privacy and anonymity
Which is more important: privacy or anonymity?
Neither is more important than the other, and their importance depends entirely on your individual needs. Privacy focuses on controlling your personal data, making it more important for daily web browsing. However, anonymity is about being unidentifiable, making it crucial for whistleblowing and protecting journalism sources.
Can you have privacy without anonymity, or vice versa?
Yes, you can have privacy without anonymity. For instance, a confidential conversation with a known friend is private but not anonymous, and banking transactions are private yet tied to your identity. Conversely, you can have anonymity without privacy, such as using a pseudonym online. People might see what you post, but they don’t know it’s you behind it.
Is privacy defined as the right to be anonymous?
No, privacy is not strictly defined as the right to be anonymous. It’s a broader concept encompassing the right to control your personal information, activities, and interactions. On the other hand, anonymity is a specific state of being unidentifiable.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN