What is computer networking and how VPNs fit in

Computer networks form the backbone of modern digital communication. Learning how these networks operate will help you better understand the modern digital landscape and make smarter decisions about privacy and security.
In this comprehensive guide, we explore computer networks and how they relate to virtual private networks (VPNs). It covers network types, essential components, security measures, common protocols, and practical troubleshooting tips.
Introduction to computer networks
What is a computer network?
A computer network is a system that enables two or more computing devices to exchange data and share resources. It does this by establishing a shared set of communication protocols. A protocol is a set of rules that determines how data is sent, received, and interpreted.
Having a shared basis for interaction is essential for networks to function.
Privacy and security considerations in networking
By facilitating the transmission of information across physical or wireless connections, networks introduce certain risks. Data in transit is exposed to interception, modification, or corruption. Proper protections are required to keep networks safe.
This is why most computer networks adopt security measures, such as encryption, secure protocols, and access controls. Supplemental technologies like VPNs can provide additional layers of protection. Whether implemented on a device or network-wide level, VPNs enhance privacy and security by encrypting all traffic (the data moving between devices on networks).
Key networking components
Devices, transmission media, and protocols
In a network, devices are the nodes that can send, receive, or store data. These can be further divided between end-user devices and infrastructure hardware. Alongside these, transmission media provide the actual connection, while protocols dictate how the whole process works.
End-user devices are what users interact with, but they don’t play a significant role in supporting the rest of the system. Instead, other components of computer networks do most of the work, keeping devices like computers, printers, and phones connected.
Infrastructure hardware (sometimes called network devices) ensures that information reaches the correct devices. For example, routers move data between networks, while switches manage communication within a single network.
Transmission media refers to the pathways that connect devices. This includes copper and fiber cables as well as Wi-Fi and radio signals. In both cases, media is the means by which data is transmitted within and between networks.
Network protocols are the logical rules that allow devices on a network to communicate with each other using a shared framework. They define how data is formatted, transmitted, and secured. Common protocols include Transmission Control Protocol (TCP) / Internet Protocol (IP), which governs most internet communication, HTTPS for web traffic, and File Transfer Protocol (FTP) for file transfers.
The role of IP addresses and DNS
An IP address is a unique number assigned to every device within a network. It works like a home address, telling other devices where to send data. When one device communicates with another, the data includes the IP addresses of both the sender and recipient, ensuring that information reaches the correct destination.
In networking, there are various kinds of IP addresses. Many devices have more than one. Most devices have a local or private IP that is used within a local network, and a separate public IP that identifies it on the wider internet.
While devices communicate using only numerical IP addresses, this is inconvenient for humans. Instead of memorizing numeric codes, the Domain Name System (DNS) allows people to use words to access websites, other devices, and more. For example, a user enters expressvpn.com into their browser, and DNS will automatically translate this into the appropriate IP address and connect the user to the server holding our site’s resources.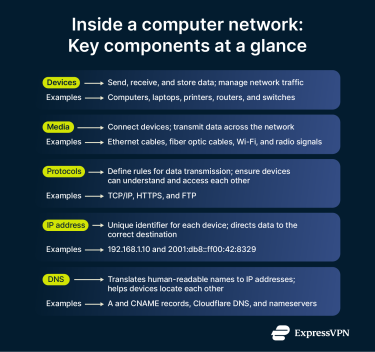
Types of networks and where VPN fits in
There are many different types of computer networks that differ in scale, function, and shape (also referred to as network topology). Networks range from two-device media sharing setups to the internet itself.
PAN, LAN, WAN
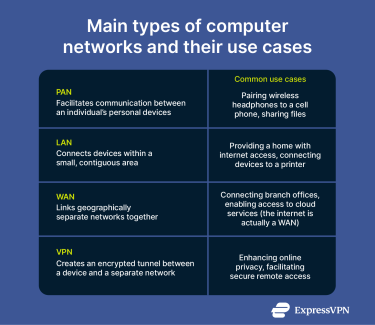
One way of categorizing networks is based on the physical area they cover. From this perspective, common network types include:
- Personal area network (PAN): Relying on technologies such as Bluetooth and Near Field Communication (NFC), PANs connect devices within a very limited radius. They facilitate quick, direct communication between personal devices for syncing files, notifications, or media. For example, a PAN may be used to link a laptop to a wireless mouse and headphones.
- Local area network (LAN): A LAN links computers and other devices within a small, localized area, such as a home, school, or small office. Most LANs are owned and managed by a single individual or a small team. They usually provide devices with a connection to the wider internet as well as links to each other. The internal connection is often used to share files across devices and connect printers to computers.
- Wide area network (WAN): A WAN connects devices across a larger geographic area. This may include different buildings in the same city, or sites spread across multiple continents. Essentially, a WAN is a network made up of interconnected smaller networks. They’re most often deployed by businesses, universities, governments, and other organizations. The internet itself is the largest WAN, connecting millions of smaller networks worldwide.
What is a VPN network?
VPNs effectively serve as a virtual overlay on top of other networks.
A VPN works by connecting the user to a secure server, creating an encrypted tunnel through which all online traffic is routed. This adds a layer of separation between the device and the internet. As a result, external devices and websites can’t see information about the user’s actual network; they’ll instead see details associated with the VPN server.
In corporate settings, organizations typically use two main types of VPNs: site-to-site VPNs, which connect entire networks (such as branch offices), and remote-access VPNs, which let individual employees securely connect to the company’s private network.
Why VPNs matter for network security
The major advantage of VPNs, whether personal or corporate, is enhanced security. While many networks transmit data in plaintext, VPNs encrypt it, ensuring that transmitted information cannot be intercepted or altered in transit. Routing traffic through an encrypted tunnel to a remote server protects users from potential eavesdroppers, including network administrators, internet service providers (ISPs), and cybercriminals, and hides their real IP address and location.
Beyond security, VPNs also facilitate communication between devices. Instead of creating a new network, they provide secure access to existing ones with added privacy. Corporate VPNs are more flexible than traditional network setups because they don’t require dedicated physical infrastructure, such as leased lines or direct cabling, between locations. This flexibility allows devices in different places to communicate as if they were on the same local network. In this sense, VPNs function somewhat like PANs, creating a sense of proximity between devices, even across the globe, thanks to extensive server networks.
VPNs vs. other secure networking methods
VPN vs. proxy servers
Both VPNs and proxy servers route traffic through an intermediary server, but they differ greatly in scope, security, and reliability.
Unlike VPNs, most proxies don’t encrypt traffic. This leaves data vulnerable to interception, monitoring, or manipulation. There is nothing to stop a web proxy operator from logging all transferred data (even if the proxy has encryption; the operator can still access all data in unencrypted form), and free proxies have even been known to inject ads.
For these reasons, using proxies is generally not recommended. Never enter a password or any sensitive information while using a proxy, as you can’t be sure if the connection is secure. Socket Secure 5 (SOCKS5) is a generally safer way to use proxy technology, but even this protocol does not encrypt data by default.
VPN vs. zero-trust networks
Both VPNs and zero-trust networks are designed to protect data and control access, but they take fundamentally different approaches. For one, zero-trust networks apply primarily to organizations, while VPNs provide real benefits in both consumer and enterprise settings.
Corporate VPNs provide strong encryption, but most implementations are designed to secure data in transit rather than to authenticate or monitor every internal connection.This can introduce risks if access controls aren’t properly managed.
A zero-trust network, on the other hand, is built on the principle of least privilege. No user, device, or action is trusted implicitly. Rather, access is granted only after verification, and restricted to only specific resources, often for a specific amount of time. This makes it harder for attackers to move laterally within network, even if they gain access.
VPNs remain simpler and more cost-effective solutions for consumers. In business contexts, they work well for smaller networks and legacy systems, while zero-trust networks require significant system changes and continuous oversight. A zero-trust approach is often more suitable for large businesses or organizations handling highly sensitive data.
VPN vs. MPLS and SD-WAN
For organizations, Multiprotocol Label Switching (MPLS) and Software-defined Wide Area Networks (SD-WAN) can fulfill a broadly similar role to a VPN, but they differ in cost, flexibility, and control.
MPLS
Under MPLS, the user accesses a provider’s private network rather than the public internet. Data packets are labeled to follow predefined routes through the network. As each router in the data packet’s journey no longer needs to make an independent routing decision, MPLS provides more consistent performance and reliability than a standard network. It’s therefore useful for time-sensitive applications like Voice over Internet Protocol (VoIP) and video conferencing.
However, unlike VPNs, MPLS doesn’t encrypt traffic by default. Instead, data is kept safe by isolating it from other users on the provider’s network. This requires dedicated infrastructure, which adds significant costs. It can also be challenging to implement and scale, with coordination being required along with additional hardware.
SD-WANs
SD-WANs take the idea of a traditional WAN further by using software to manage and optimize connections between multiple sites, abstracting the underlying physical infrastructure. An SD-WAN can route traffic across a mix of broadband internet, LTE/5G, and existing MPLS lines, automatically choosing the most suitable path for each data flow. For example, non-critical data may use cheaper and lower-quality paths, while critical data is sent through the best available option.
This makes SD-WAN efficient, reliable, and easy to scale, particularly for businesses with several offices, cloud applications, or distributed teams.
Comparatively, site-to-site VPNs are often harder to scale and adapt for multiple sites because traffic often follows a single, fixed path. That said, corporate VPNs are still an effective way for companies to allow remote employees to securely access resources. For these reasons, many organizations combine VPNs with SD-WAN technology, with the VPNs providing encryption and the SD-WAN managing traffic.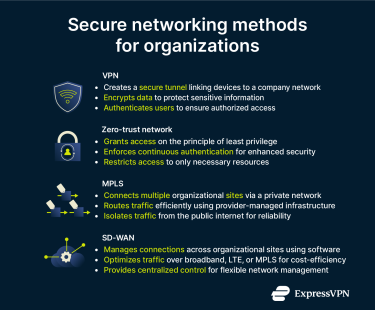
Common VPN protocols
VPN protocols are the rules and procedures that determine how data is transmitted and secured between your device and the VPN server. Different protocols balance security, speed, and compatibility in various ways, so understanding them is key to choosing the right VPN setup for your network.
OpenVPN, IKEv2, WireGuard
There are a few options that stand out as the most widely used VPN protocols, including:
- OpenVPN: A well-established and secure protocol that’s compatible with many devices and networks. It can be configured to favor reliability or speed and works effectively with most firewalls.
- Internet Key Exchange version 2 with Internet Protocol Security (IKEv2/Psec): A stable protocol that maintains connections even when networks change, offering consistent performance and strong security. IKEv2 handles key exchange but does not provide encryption on its own, so it’s almost always paired with IPsec.
- WireGuard: A modern, lightweight protocol designed for speed and efficiency. Its streamlined design makes it faster than older protocols while still providing strong encryption.
Which protocol is right for your network?
The protocol that’s best for your network depends on your priorities. Organizations select protocols to suit their workflow and network environment. For individuals, many VPN providers support multiple protocols, allowing users to test which is fastest.
Environments that emphasize proven security and broad compatibility often rely on OpenVPN. But individuals who switch between networks frequently may prefer IKEv2/IPsec over OpenVPN because it reconnects quickly and maintains stable connections across Wi-Fi and cellular networks. Finally, teams that prioritize speed and low latency might opt for WireGuard.
In home-use settings, proprietary protocols can offer distinct advantages. ExpressVPN’s Lightway protocol, for example, combines fast performance, reliability, and strong security, making it a versatile option for users who need both privacy and efficiency.
Troubleshooting in computer networking
How to troubleshoot network problems
Network issues can arise from a wide variety of sources, ranging from hardware failures to misconfigurations. Due to the large number of possibilities, following a standard troubleshooting procedure is a good idea when searching for an effective solution. The steps below provide a systematic approach to diagnosing and resolving network problems:
- Identify the problem: Gather information from users and network logs to determine the scope of the issue. Identify whether it affects a single device or multiple users to narrow down potential causes. You can also use command-line utilities, packet analyzers (like Wireshark), and performance monitors (like SolarWinds’ Network Performance Monitor) to help find the issue.
- Establish a hypothesis: Based on gathered information, consider possible causes such as hardware failures, configuration errors, or external disruptions.
- Test the hypothesis: Run tests to confirm or rule out suspected causes. Examples include swapping cables to rule out physical issues or adjusting configurations.
- Implement a solution: Apply fixes corresponding to the identified root cause. Solutions may involve replacing hardware, updating configurations, or correcting software settings.
- Monitor the network: After implementing the solution, monitor network performance to ensure the problem is resolved.
FAQ: Common questions about computer networking
Is a VPN part of computer networking?
Yes, VPNs fit into the broader category of computer networking. A VPN serves as an intermediary between your device and other networks and brings various security and privacy benefits. Individuals use VPNs to protect personal data and browse the internet privately, while businesses deploy them to secure remote access and internal communications across distributed teams.
How does VPN encryption work?
VPN encryption secures data by rendering it unreadable as it travels across the network, ensuring the information remains protected even if it’s intercepted. Encryption protocols, such as OpenVPN, IKEv2/IPsec, and WireGuard, determine how data is encrypted and decrypted.
Does a VPN protect against all threats?
No, VPNs don’t protect against every type of cyberattack. Their primary role in home networking is to secure data while it’s in transit and hide your IP address. For businesses, corporate VPNs support remote access. But VPNs cannot prevent malware infections, phishing attacks, or device-level vulnerabilities, so safe computing practices, firewalls, and antivirus software remain essential.
Can a VPN be used on all networks?
VPNs can be used on most networks, but some may block VPN traffic.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN