WireGuard vs. OpenVPN: Which VPN protocol is better in 2025?

When it comes to choosing between WireGuard and OpenVPN, most people think only about speed. But there’s a lot more to consider. These two VPN protocols differ in performance, security, and compatibility, but they also share some surprising similarities you might not expect.
In this guide, we’ll break down how WireGuard and OpenVPN compare, where each works best, and how they’re used in ExpressVPN.
What is a VPN protocol?
Let’s start with the basics. A VPN protocol is a set of rules that decide how your data moves through a VPN tunnel and how it’s protected along the way. It’s what determines how your online traffic is handled from the moment it enters the tunnel until it comes out the other side.
Why VPN protocols matter for privacy and performance
The protocol your VPN uses has a big impact on both privacy and performance. Some protocols are built to disguise VPN traffic so it looks like regular internet activity, which might be helpful on restrictive networks. Others focus on finding the quickest, most efficient route between servers to give you faster speeds.
That’s why the VPN protocol you choose plays a big role in how fast, secure, and private your connection will be.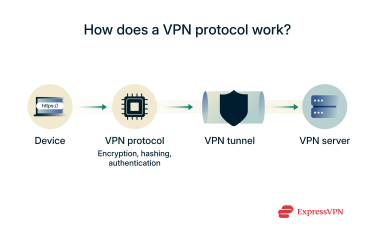
What is WireGuard?
WireGuard is a VPN protocol designed for speed and efficiency, using a lean codebase (around 4,000 lines in its Linux implementation) and modern cryptographic algorithms optimized for performance.
First released in 2015 by Jason A. Donenfeld, WireGuard was created to simplify and improve upon older, more complex VPN protocols like IPsec and OpenVPN. Initially integrated only into the Linux kernel, it has since expanded to most major operating systems, including macOS, Android, Windows, iOS, and BSD.
How does WireGuard work?
WireGuard creates a secure tunnel between your device and a remote VPN server. It encrypts your data using the ChaCha20-Poly1305 encryption and authentication algorithm, preventing outsiders from reading or tampering with your traffic.
Unlike older VPN protocols, WireGuard uses a fixed set of modern, pre-selected cryptographic algorithms for encryption, authentication, hashing, and key exchange. This makes the codebase lightweight, easy to audit, and highly secure.
By default, WireGuard sends traffic over UDP, which allows for faster performance compared to TCP-based VPNs. While UDP doesn’t guarantee delivery by itself, your apps and protocols (like TCP inside the tunnel) handle retransmissions, so your data still arrives reliably.
Learn more: Read our article on TCP vs. UDP to understand the key differences and best use cases.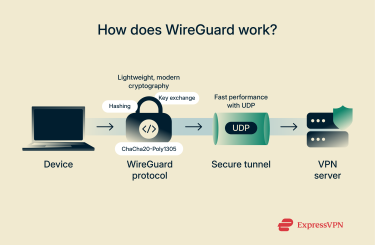
Pros and cons of using WireGuard
WireGuard comes with several strong advantages:
- Modern cryptography: Uses streamlined, up-to-date encryption that provides robust security with high performance.
- Lightweight design: With only a few thousand lines of code, it’s easier to audit, maintain, and fix compared to bulkier protocols like OpenVPN.
- High performance and privacy: Delivers reliable privacy protection without noticeably slowing down your connection.
That said, there are also a few drawbacks worth keeping in mind:
- Limited obfuscation: WireGuard doesn’t aim to hide VPN traffic from deep packet inspection. Obfuscation can be added on top through third-party tools, but it isn’t built into the protocol itself.
- UDP-only by design: WireGuard doesn’t support tunneling over TCP, as doing so would cause poor network performance. This can make it harder to connect in environments that block or heavily restrict UDP traffic.
- No default post-quantum protection: WireGuard isn’t post-quantum secure by default, but it can be hardened with a pre-shared key. That’s what ExpressVPN did: adding a hybrid ML-KEM key exchange to make it resistant to quantum decryption threats.
What is OpenVPN?
OpenVPN is a widely used, open-source VPN protocol that has been around since 2001. Known for its reliability and versatility, it’s long been considered one of the most secure ways to create encrypted VPN tunnels.
Unlike WireGuard’s minimalist design, OpenVPN’s open-source codebase spans roughly 70,000 lines, which makes it more complex but also highly configurable and well-tested over time.
How does OpenVPN work?
OpenVPN establishes a secure, encrypted tunnel between your device and a remote VPN server, protecting all data that passes through it. Instead of relying on a fixed cryptographic setup, it uses the TLS/SSL framework, the same foundation used to secure HTTPS connections.
Since Access Server 2.5 and OpenVPN client 2.4, the default cipher has been AES-256-GCM, though newer builds also support ChaCha20-Poly1305 for faster performance on modern CPUs and mobile devices. This flexibility, often called algorithm agility, lets OpenVPN negotiate the best available cipher based on configuration and platform support.
This flexibility extends to how OpenVPN handles network traffic. It can operate over either TCP or UDP, allowing you to choose between more stable but potentially slower TCP connections or faster UDP connections that may be less reliable on restrictive networks.
However, all this adaptability comes at a cost. The protocol’s size and complexity can slow down execution and make it harder to audit, increasing the potential for bugs or vulnerabilities. That’s one reason newer options like WireGuard have gained attention: they offer a leaner, faster alternative with simpler code.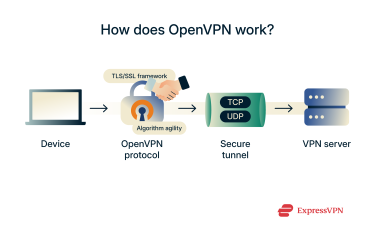
Pros and cons of using OpenVPN
Some of the biggest advantages of the OpenVPN protocol include:
- Broad compatibility: Works across almost all platforms and supports a wide range of cryptographic algorithms.
- Flexibility: Lets you choose between UDP and TCP, as well as different cryptographic algorithms, depending on whether you need speed, stability, or stronger security.
- Mature and battle-tested: With over two decades of use, OpenVPN is widely trusted and supported by most VPN providers.
Even so, OpenVPN isn’t without its drawbacks:
- Complex setup: Its extensive feature set can make configuration and deployment more challenging, especially for less experienced users.
- Heavy codebase: With tens of thousands of lines of code, OpenVPN is harder to audit, maintain, and troubleshoot compared to lightweight protocols like WireGuard.
- Performance tradeoffs: Its complexity and reliance on heavier cryptographic layers can lead to slower speeds, particularly on lower-end devices or networks with high latency.
WireGuard vs. OpenVPN: Key differences explained
The key differences between WireGuard and OpenVPN can help you decide which protocol better fits your privacy and performance needs. The table below offers a quick overview, followed by more detailed explanations later in the article.
| WireGuard | OpenVPN | |
| Speed | Generally faster thanks to its lightweight code and kernel-level integration | Slower due to a larger codebase and TLS overhead |
| Encryption design | Fixed, modern cryptographic suite (ChaCha20-Poly1305, Curve25519, BLAKE2s, HKDF) | Flexible, negotiable algorithms via TLS/SSL (e.g., AES, RSA) |
| Codebase size | ~4,000 lines (Linux kernel module, excluding crypto primitives) | ~70,000 lines (open-source version) |
| Auditability | Easier to audit and review due to its small, simple design | More difficult to audit fully because of its complexity |
| Compatibility | Android, iOS, macOS, Windows, Linux, BSD, and more | Android, iOS, macOS, Windows, Linux, BSD, and more |
| Transport layer | UDP only | UDP and TCP |
| Ease of manual setup | Simple and quick on most platforms | More complex and configuration-heavy |
| Best suited for | Speed, efficiency, and modern deployments | Flexibility, legacy support, and enterprise use |
Speed and performance comparison
In most tests, WireGuard delivers faster speeds and lower latency than OpenVPN. Its minimalist design allows for quicker encryption and more efficient tunneling, while OpenVPN’s larger, more flexible framework introduces extra processing steps.
OpenVPN can still perform well, especially when stability is prioritized with TCP, but for raw speed and responsiveness, WireGuard usually comes out ahead.
In a quick test using ExpressVPN with the same server location (U.K. – London), both protocols delivered similar download speeds (around 90 Mbps), but WireGuard showed a clear edge in responsiveness. Latency dropped from 113 ms on OpenVPN (TCP) to just 40 ms on WireGuard, and jitter was eliminated entirely.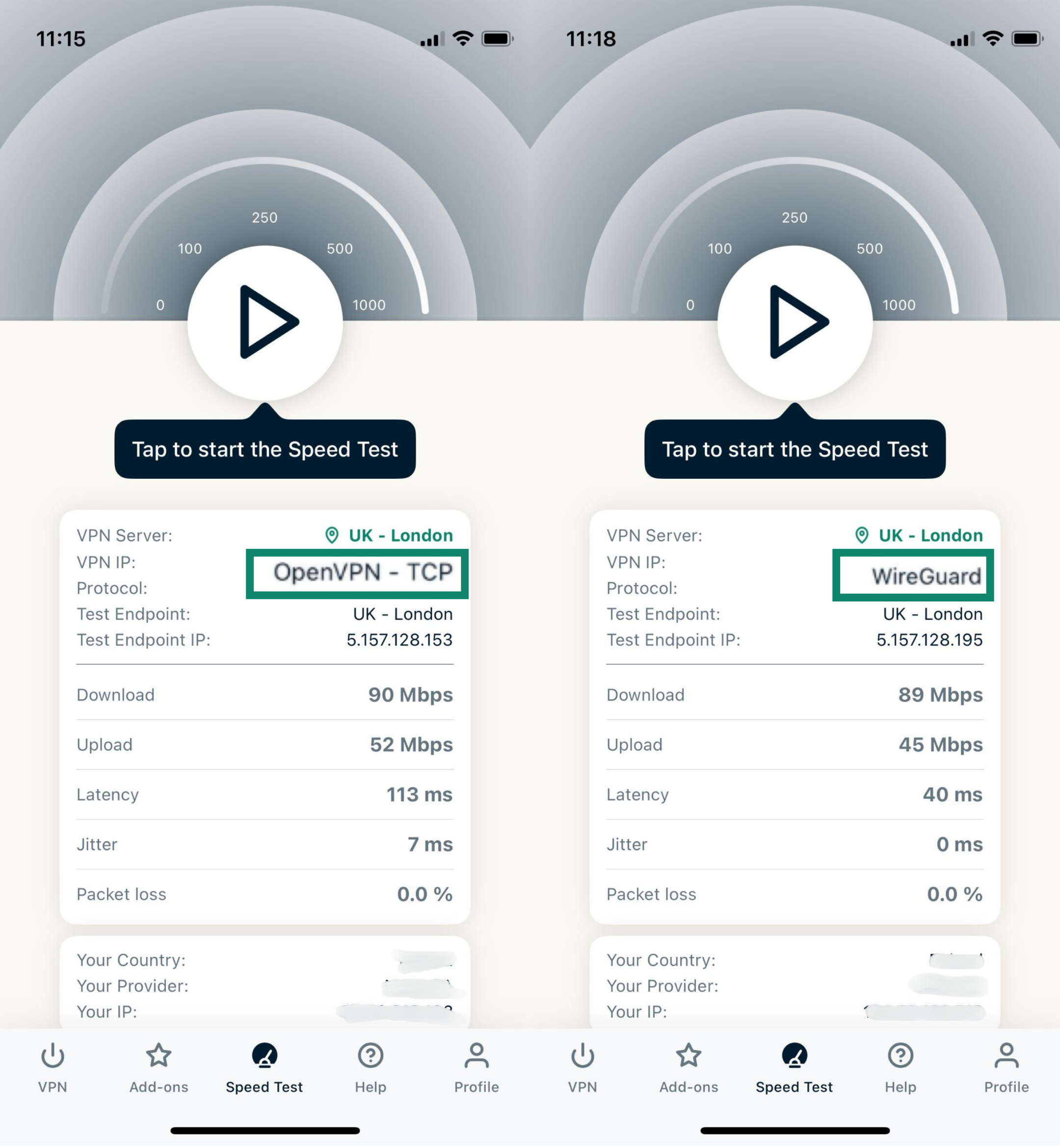
That means web pages and apps respond faster, even if raw throughput appears similar. These numbers reflect how WireGuard’s lean design and use of UDP translate into a more efficient, real-world browsing experience.
Encryption and cryptographic standards
One of WireGuard’s main strengths lies in its simplicity: it uses a fixed, modern set of cryptographic algorithms that are fast, secure, and easy to audit. OpenVPN, by contrast, supports a broad range of encryption and authentication methods through the TLS/SSL framework. This makes it highly compatible with different systems but also adds complexity and overhead.
| WireGuard | OpenVPN | |
| Encryption / AEAD | ChaCha20-Poly1305 | AES-GCM, AES-CBC, ChaCha20-Poly1305, Blowfish, Camellia, 3DES (depending on TLS library and config) |
| Authentication/integrity | Poly1305 (integrated into AEAD) | HMAC with SHA-1, SHA-2, Poly1305, and others |
| Hashing | BLAKE2s | SHA-1, SHA-2, MD5, and others (based on chosen cipher suite) |
| Key exchange | Curve25519 (ECDH via the Noise framework) | RSA, Diffie-Hellman, ECDH, Ed25519, X25519, etc. |
| Key derivation | HKDF | TLS key derivation (varies by cipher suite) |
This flexibility allows OpenVPN to integrate with older or specialized systems and adapt to enterprise needs. WireGuard, meanwhile, keeps things consistent: every implementation uses the same well-defined cryptographic suite, which simplifies deployment and improves performance but leaves less room for customization.
Security and auditability
Both WireGuard and OpenVPN are open-source, meaning their code is publicly available for anyone with the right expertise to review. This transparency helps ensure the protocols deliver on their promise of secure, encrypted data transfer.
That said, WireGuard is much easier to audit thanks to its lean codebase. In fact, a single skilled engineer could reasonably review WireGuard’s code, while OpenVPN’s much larger codebase would require a team of experts.
The reassuring part is that neither protocol has known privacy flaws, so both are considered safe to use. The difference lies in maturity: OpenVPN has been around for over two decades and has been tested and audited extensively in real-world conditions, which gives it an edge in long-term trust.
Compatibility across devices and platforms
WireGuard started as a Linux-centric protocol, but today it’s available on nearly all major operating systems, like Android, iOS, Windows, macOS, Linux, and BSD. That said, its fixed cryptographic choices mean a system must support those primitives (e.g., ChaCha20, Curve25519) in order to run WireGuard, which can make deployment harder in niche or legacy environments.
Most VPN services allow users to switch between OpenVPN or WireGuard on smartphones (Android and iOS), computers (macOS, Windows, and Linux), and even smart TVs (like Google TV). But when it comes to routers, OpenVPN has a longer history of native support and widespread compatibility, whereas WireGuard often requires more hands-on work: flashing custom firmware (like OpenWRT or DD-WRT) or using routers with built-in WireGuard support.
In short: OpenVPN’s extensive configurability and long software heritage give it broader compatibility in diverse environments. WireGuard, in contrast, favors a lean, modern stack that excels on supported platforms but may need extra effort on less common ones.
Privacy and data retention
WireGuard’s design requires the server to remember the client’s endpoint (IP + port) during a session so it knows where to send traffic. This information isn’t stored permanently; it’s dropped once the session ends or the server reboots, but it does exist in memory during the active session. That means, in theory, it could be exposed if the server were compromised.
OpenVPN, on the other hand, uses TLS-based handshakes and doesn’t inherently rely on maintaining the same kind of live session state tied to a client’s IP. That design reduces exposure to the specific issue of in-memory endpoint data retention.
Of course, the biggest factor in privacy is your VPN provider’s logging policy. Any provider could opt to log connection metadata under either protocol.
ExpressVPN, for example, enforces a strict no-logs policy. Initially, this led us to avoid WireGuard in favor of building our own protocol, Lightway, which was designed to deliver strong privacy with faster connection speeds and seamless reliability across devices. However, ExpressVPN has since implemented WireGuard with additional safeguards.
Setup and ease of use
For most people, using WireGuard or OpenVPN is simple because they’re built into VPN apps. With ExpressVPN, you can switch between the protocols in just a couple of taps from the home screen.
When it comes to manual setup, WireGuard tends to be quicker thanks to its minimal configuration requirements. OpenVPN offers far more parameters and customization, which can make setup more involved, especially for advanced or enterprise deployments. In practice, though, anyone with basic VPN experience can configure either protocol without much difficulty.
Learn more: You might want to check out our step-by-step guide on how to create a VPN by yourself.
Codebase size and maintainability
OpenVPN’s codebase is significantly larger; roughly 20 times the size of WireGuard’s. This complexity stems from its support for numerous encryption standards, tunneling methods, and operating systems. While that makes OpenVPN highly flexible, it also makes the code harder to maintain, audit, and optimize.
WireGuard, on the other hand, was built for simplicity. Its core implementation has only around 4,000 lines of code (in the Linux kernel module), making it far easier to review and manage.
To put it in perspective: maintaining OpenVPN is like keeping a vast 200 ft × 400 ft room filled with furniture, electronics, and gadgets organized, while WireGuard is a minimalist 20 ft × 20 ft room with just one clean, well-placed table. The smaller, simpler space is always easier to maintain.
Transport layer and ports used
As we already explained, OpenVPN can run on both UDP and TCP, giving you more flexibility. WireGuard, by design, only runs on UDP, since it’s optimized for speed and lower latency.
It’s not just about speed, though. TCP can be configured to use Port 443 (the same port as HTTPS), which makes it much harder for firewalls to block without breaking normal web traffic. UDP, which WireGuard relies on, doesn’t have this advantage and is more likely to be restricted on heavily censored or tightly controlled networks.
Learn more: For a broader comparison, take a look at our VPN protocols guide, where we cover more than just WireGuard and OpenVPN.
WireGuard vs. OpenVPN: Similarities
Although WireGuard and OpenVPN take different paths to securing your connection, they share several core strengths that make them both trusted and reliable choices:
- Open-source code: Both are fully open source, meaning anyone can review, audit, or even contribute to their development. This transparency helps maintain trust and security.
- Cross-platform support: Each works across major operating systems, including Windows, macOS, Linux, Android, and iOS, and even on BSD or select smart TVs.
- Strong cryptography: Both rely on modern, well-vetted cryptographic standards for encryption, authentication, and hashing.
- Perfect forward secrecy: PFS is built into modern VPN protocols like WireGuard and supported by OpenVPN through ephemeral key exchange (DHE/ECDHE). VPN providers, such as ExpressVPN, enable it by default, ensuring that even if a key were ever compromised, past sessions would remain secure.
- Proven security record: Neither protocol has any known vulnerabilities in the current version, and both have undergone years of scrutiny from the open-source and security communities.
- Extensibility: Each can be enhanced with plugins, scripts, or modules to add functionality beyond the base protocol.
Which VPN protocol is right for you?
Both OpenVPN and WireGuard are secure, proven VPN protocols that protect your online traffic effectively. However, their design differences make each one better suited for certain tasks.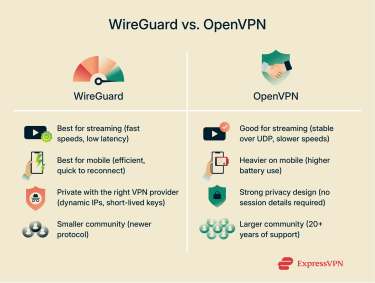
For streaming: Which is better for streaming platforms?
WireGuard usually has the edge when it comes to streaming. Its lightweight design and modern encryption allow for faster speeds and lower latency, meaning less buffering and a smoother viewing experience.
That doesn’t mean OpenVPN can’t deliver smooth playback, especially if you use it over UDP. But compared to WireGuard, it tends to cause a bigger drop in base internet speed, which can affect streaming performance on high-resolution content.
For privacy-conscious users: Which offers more anonymity?
OpenVPN has a slight edge in privacy by design, since it doesn’t need to retain identifying session details (like your IP address) when you connect to a VPN server. That said, your real level of privacy still depends on your VPN provider’s policies and safeguards.
With the right provider, WireGuard can be just as private. For example, ExpressVPN uses dynamic IP assignment and short-lived authentication keys in its WireGuard setup, along with post-quantum encryption. This approach ensures your sessions can’t be tied back to you and helps future-proof your data security.
For mobile and low-latency usage: Which is better for speed and battery efficiency?
WireGuard is generally the better choice for mobile devices and latency-sensitive tasks. It’s lightweight, quick to reconnect, and handles network changes (like switching from Wi-Fi to mobile data) more smoothly than OpenVPN.
Unlike OpenVPN, which runs in user space, WireGuard is integrated directly into the operating system kernel on platforms like Android. This means it can process network packets without constantly passing them between the app layer and the kernel (a process called context switching). Reducing that back-and-forth significantly lowers CPU overhead and helps the device spend more time in low-power states, leading to better performance and battery life.
OpenVPN, by contrast, requires more user-space processing for every packet, which increases CPU load and energy use. WireGuard’s streamlined, kernel-level design makes it the more efficient option for everyday mobile use.
For long-term reliability: Which protocol has better community support?
Both WireGuard and OpenVPN enjoy strong community backing, but OpenVPN has the larger and more established support base. That’s not surprising, given it’s been around for more than 20 years.
OpenVPN’s GitHub and community forums tend to be very active, partly because the protocol’s larger and more complex codebase requires ongoing tweaks, updates, and platform-specific fixes. WireGuard, on the other hand, often sees less visible development activity, not because it’s neglected, but because its leaner design leaves fewer moving parts to maintain once it’s working properly.
Learn more: Take a look at our WireGuard vs. IPsec comparison for another perspective.
ExpressVPN’s approach to WireGuard and OpenVPN
ExpressVPN supports both WireGuard and OpenVPN, allowing users to switch between them based on their needs. It also lets you choose between OpenVPN UDP and OpenVPN TCP, offering flexibility for different network conditions and performance preferences.
ExpressVPN has also gone a step further by building its own optimized version of WireGuard, designed to fix the protocol’s weaknesses while keeping its speed and efficiency. These improvements include:
- Post-quantum security: ExpressVPN’s WireGuard implementation adds ML-KEM, a post-quantum key exchange algorithm, to protect against future quantum decryption threats.
- Dynamic IPs: Each session uses rotating internal IPs, preventing the static address assignments that could otherwise expose a user’s identity.
- Short-lived keys: Ephemeral encryption keys and temporary session IDs are used for every connection, making long-term correlation or tracking far more difficult.
- User authentication: Since WireGuard doesn’t natively include authentication, ExpressVPN adds short-lived, token-based access credentials to verify users securely.
In short, ExpressVPN’s version of WireGuard strengthens privacy and security without sacrificing the performance gains that make WireGuard popular in the first place.
How to switch between WireGuard and OpenVPN on mobile (iOS and Android)
In the example below, we’ll use ExpressVPN’s iOS app, but the steps are almost identical on Android.
- Open the ExpressVPN app on your phone.
- Tap Profile in the bottom navigation bar.
- Select VPN Protocol.
- Choose WireGuard, OpenVPN - UDP, or OpenVPN - TCP depending on your preference.
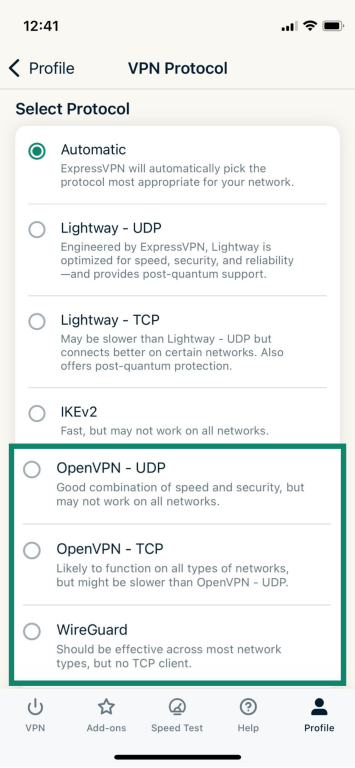
- If prompted, tap CHANGE ANYWAY to confirm.
- Return to the VPN home page and connect to any server of your choice.
If WireGuard or OpenVPN options aren’t available, you may need to disable ExpressVPN Advanced Protection first.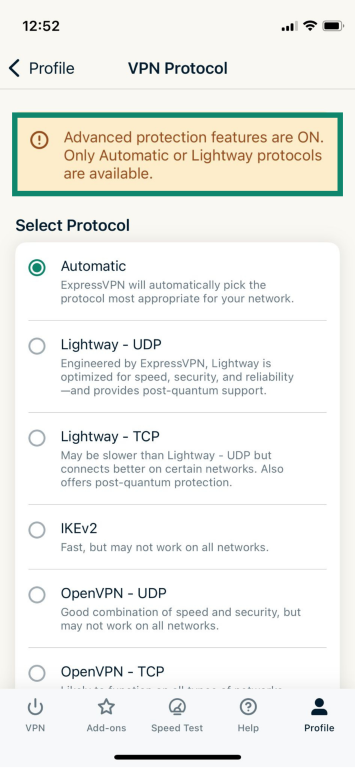
Here’s how:
- Tap Add-ons in the bottom ribbon of the ExpressVPN mobile app.
- Toggle off any activated option under Advanced Protection.
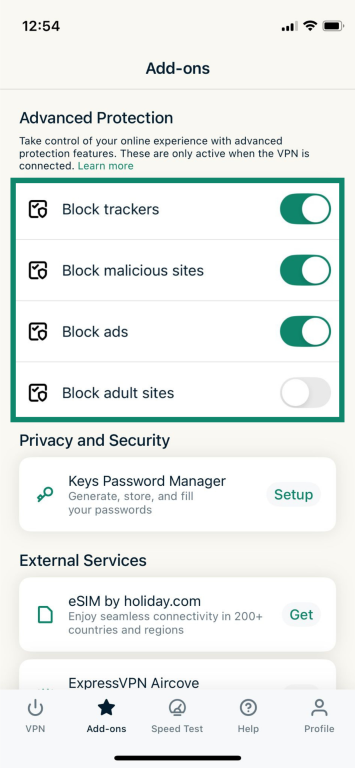
- Go back and follow the steps above to select your protocol.
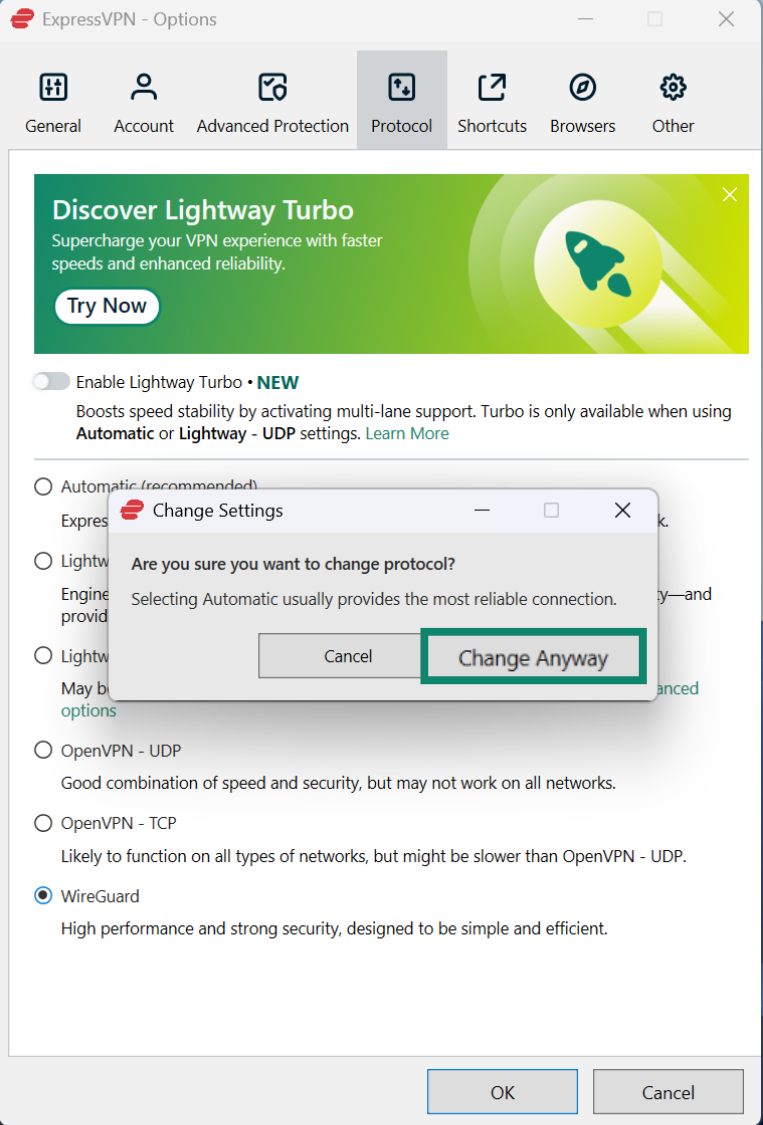
How to switch between WireGuard and OpenVPN on Windows
- Open the ExpressVPN app and click the hamburger menu in the upper-left corner.
- Choose Options.
- Select Protocol.
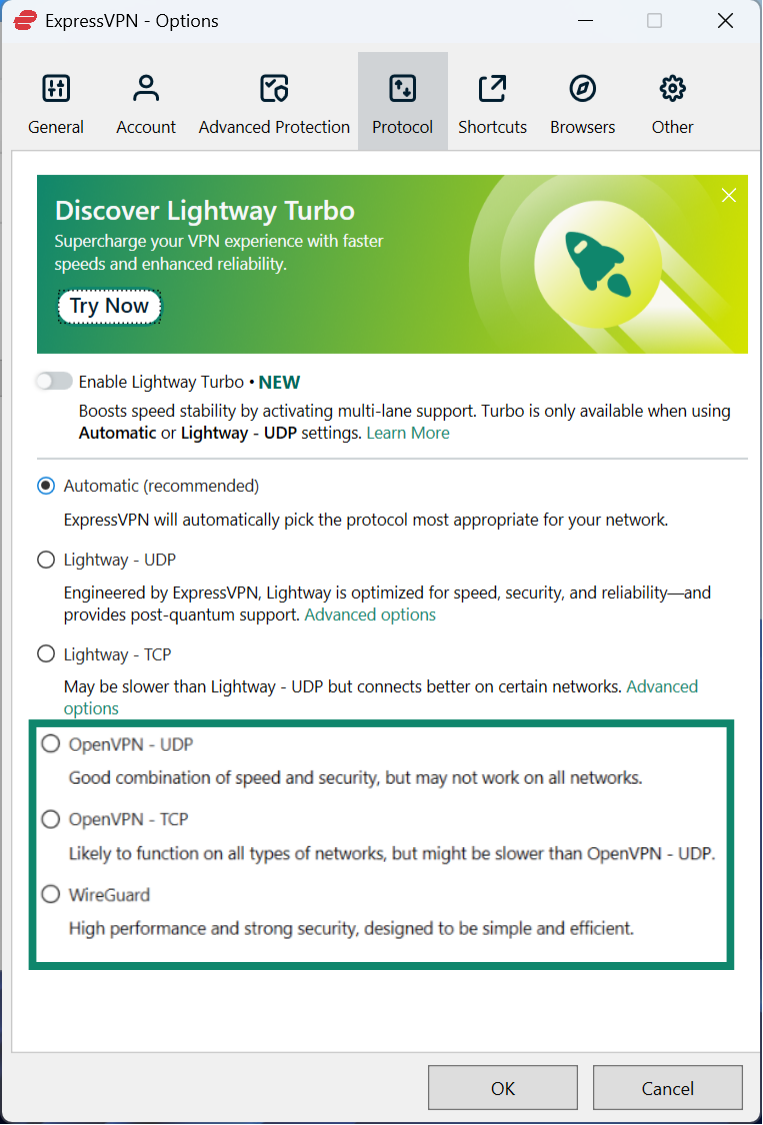
- According to your preference, choose OpenVPN - UDP, OpenVPN - TCP, or WireGuard.
- Confirm your choice by clicking Change Anyway.
If you can’t select your preferred protocol, open Advanced Protection and turn off the boxes under Threat Manager and Ad blocker.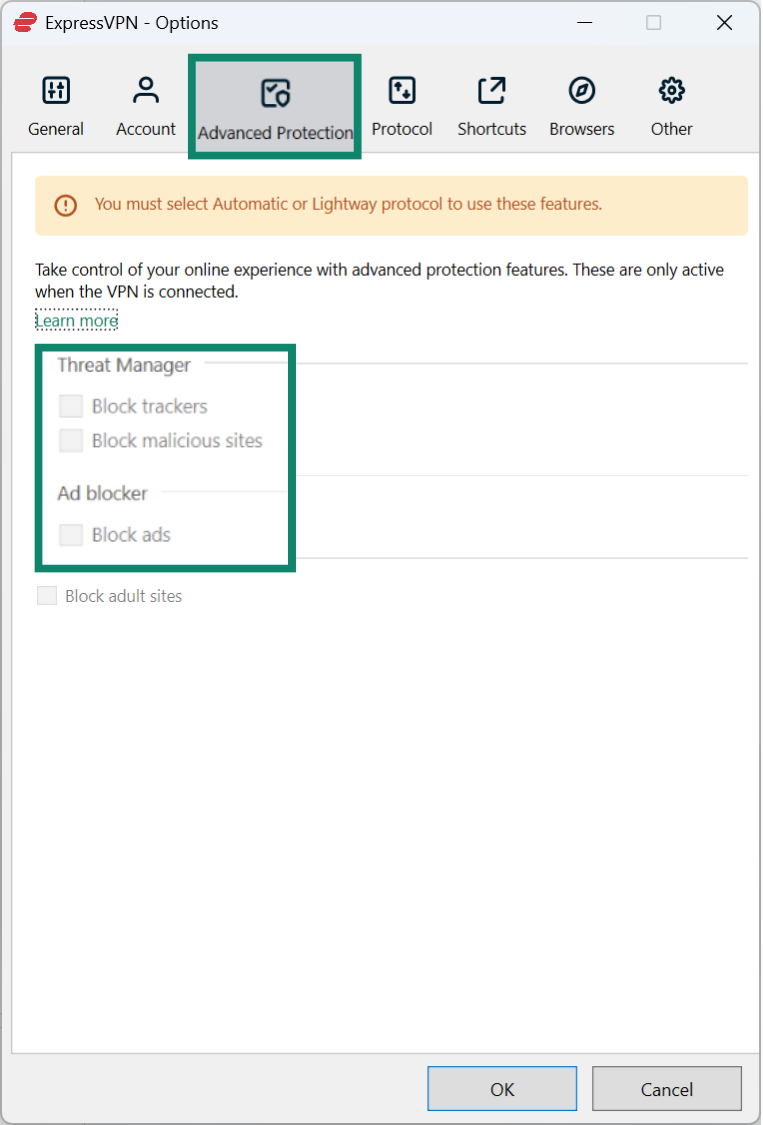
Note: Post-quantum WireGuard is now available on iOS, Android, and Windows. macOS support is coming soon.
FAQ: Common questions about WireGuard vs. OpenVPN
Is WireGuard VPN detectable?
WireGuard traffic can sometimes be detected because it uses the UDP protocol and has a recognizable packet structure. On restrictive networks or under deep packet inspection (DPI), it may be flagged as VPN traffic. However, many VPN providers add obfuscation techniques on top of WireGuard to make it harder to distinguish from regular internet traffic.
Is WireGuard the future of VPNs?
WireGuard is widely viewed as a major step toward the future of VPN technology, and ExpressVPN’s enhanced, quantum-protected version pushes it even further. By integrating post-quantum cryptography (ML-KEM), short-lived keys, dynamic IPs, and built-in authentication, ExpressVPN has addressed WireGuard’s main privacy gaps without sacrificing its hallmark speed and simplicity.
It’s available today on iOS, Android, and Windows, with macOS support on the way, offering a glimpse of what the next generation of secure, high-performance VPNs will look like.
Is a WireGuard VPN trustworthy?
Yes, WireGuard is considered trustworthy. It’s open source, uses modern cryptographic algorithms, and has a small codebase that makes it easier to audit for security flaws. That said, trust also depends on the VPN provider’s implementation. For example, ExpressVPN has built its own enhanced version of WireGuard that adds dynamic IPs, short-lived keys, and post-quantum protection, making it even more private and secure while keeping the speed benefits.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN